The word “cryptocurrency” has two components to it – “cryptography” and “currency.” As you can imagine, cryptography is at the heart and soul of cryptocurrency. Asymmetric and symmetric encryption are the two main cryptography methods, and this guide breaks them both down. Read on for a fascinating insight into the world of cryptographic encryption!
What is Cryptography? Asymmetric vs. Symmetric encryption
Cryptography constructs and analyzes protocols to prevent outside parties from reading confidential information. Cryptography utilizes mathematics, physics, communication, information technology, and computer science. Aside from cryptocurrencies, cryptography is widely used in fields like computer passwords, military comms, and electronic commerce.
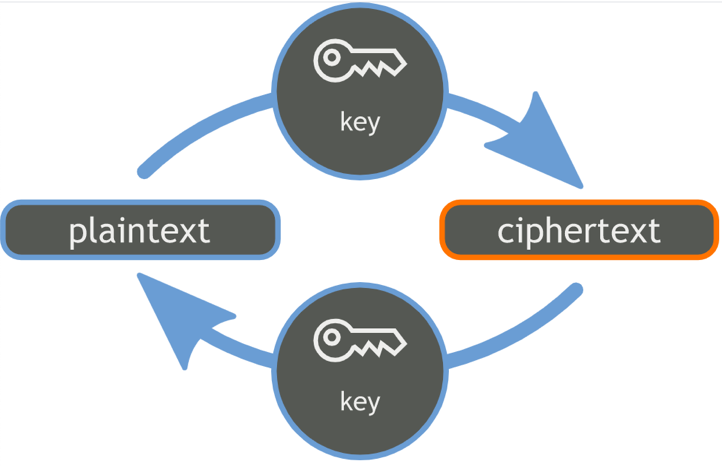
The goal of cryptography is to convert plaintext to ciphertext and back. Plain text is just a standard text written in any human-understandable language, like English, and it is easy to decode. On the other hand, the ciphertext is the encrypted version of the plaintext file, which the general user can’t understand. All this happens via the following two processes:
- Encryption: The process which turns file text to ciphertext.
- Decryption: The process that turns back ciphertext to file text.
This change from encryption to decryption and back can either happen with one key or with two. The former is symmetric encryption, while the latter is called asymmetric encryption.
Types of encryption: Symmetric Encryption
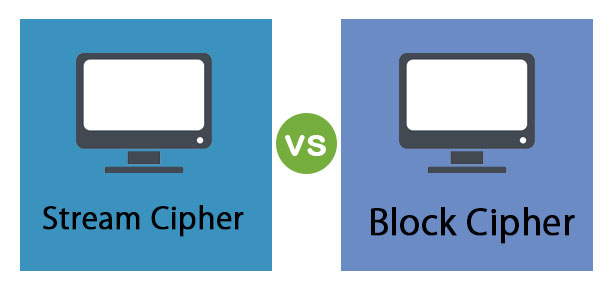
First up, we have symmetric cryptography. With this type of key cryptography, the sender and receiver of a message share a single key. This key serves as a shared secret between the two parties involved during the cryptography process. There are two kinds of symmetric encryption:
- Stream ciphers.
- Block ciphers.
Stream Ciphers
A stream cipher uses a fixed key to combine plaintext with a pseudorandom string of characters called “keystream.” It creates ciphertext by replacing each character in the plaintext with the corresponding digit of the keystream. A random seed value generates this keystream.
Let’s look at how this form of cryptography works. We will take a simple example. Suppose Alice wants to send a message “MEET” to Bob. The keystream that they both decide to use is “BBBB.”
The first thing that Alice does is numerically map on the file text and keystream (A-Z gets mapped to 0-25). So, this is how her message and keystream get mapped:
- MEET -> 12 4 4 19
- BBBB -> 1 1 1 1
Now, she adds the digits with each other and mods each digit with 26. This gives her:
- (12+1)%26 = 13
- (4+1) % 26 = 5
- (4+1) % 26 = 5
- (19+1) % 26 = 20
Now, if we map these digits to their corresponding alphabets, we get -> NFFU. This is the ciphertext that Alice sends over to Bob along with the key “BBBB.”
So, how does Bob get back the original message? Via the decryption process.
Firstly, Bob maps both the ciphertext and the key to their numerical equivalent:
- NFFU -> 13 5 5 20
- BBBB -> 1 1 1 1
Now, Bob will subtract the two and subtract each digit with 26:
- (13-1)%26 = 12
- (5-1)%26 = 4
- (5-1)%26 = 4
- (20-1)%26 = 19
Now, if map these digits to their corresponding alphabets, we get -> MEET.
So, by sharing the key, both Alice and Bob were able to go from file text to ciphertext and ciphertext to file text, respectively.
Block Ciphers
A block cipher uses a deterministic algorithm, along with a symmetric key to encrypt a block of text, instead of encrypting one bit at a time. As such, this is a faster method than stream ciphers. To visualize how it works, imagine the block cipher to be a portal that takes in two inputs – the file text and key – and gives one output – the ciphertext.
Let’s take a simple example.
- The file text is “ABCD.”
- Its key is 1.
- The block cipher takes in the whole file text, and during the encryption process, it shifts-left the file text by 1, i.e., the value of the key.
- It produces the resulting ciphertext – “BCDA.”
- To get back the file text, you enter the ciphertext into the block cipher along with the key “1” and shift-right. This time, you’ll get ABCD.
Which is better? Symmetric vs. Asymmetric encryption.
While symmetric cryptography is pretty simple to execute, there are a lot of issues with this method:
- One key to rule them all: Since the encryption and decryption key is the same, it needs to be shared very carefully. If a third-part gets their hands on the key, the information will be compromised.
- Not scalable: Another massive issue with symmetric cryptography is the lack of scalability. Eg. If Alice has to share confidential information with five people, she will have to take care of five unique keys. The more people she has secret interactions with, the more keys she will have to take care of.
Types of encryption: Asymmetric Encryption
James Ellis, a British mathematician, came up with the idea of asymmetric cryptography, i.e., using two separate keys for encryption and decryption. In this scenario, the receiver of the message is actively involved in the process as well, instead of just being a passive passenger.
To explain how asymmetric cryptography would work, Ellis gave the following example –
- Imagine a key and a padlock.
- The sender puts the message in a box and locks it up with the padlock.
- A receiver gets the locked box and opens it up with a key.
- During this process, the sender didn’t need to hand over the key to the receiver.
While this sounded pretty compelling on paper, we needed more practical implementation to execute this consistently in real-life scenarios. These implementations came in the form of – trapdoor functions and the Diffie–Hellman key exchange.
Asymmetric encryption process – How does asymmetric encryption work?
- Trapdoor function

Think of what makes a trapdoor efficient:
- It’s extremely easy to fall through it.
- It is also tough to escape once you have fallen through it.
A trapdoor function works similarly. A pretty famous example of a trapdoor function is your standard hash function. For example if we pass “100” through an SHA-256 hash generator, we will get AD57366865126E55649ECB23AE1D48887544976EFEA46A48EB5D85A6EEB4D306.
So, how is this is a trapdoor function?
- If we give you the input value “100”, it will be simple for you to hash it using an SHA-256 generator and get the output hash.
- However, if we just give you “AD57366865126E55649ECB23AE1D48887544976EFEA46A48EB5D85A6EEB4D306”, you will probably be a little lost.
How is this valid in asymmetric cryptography?
In asymmetric cryptography, we use two keys – the public key and the private key. Information gets encrypted with the public key. The process of getting the ciphertext from the plaintext and the public key is straightforward. However, getting the plaintext from the ciphertext is extremely difficult. The only thing you can do is use the decryption key, aka, the private key.
- Diffie-Hellman Key Exchange
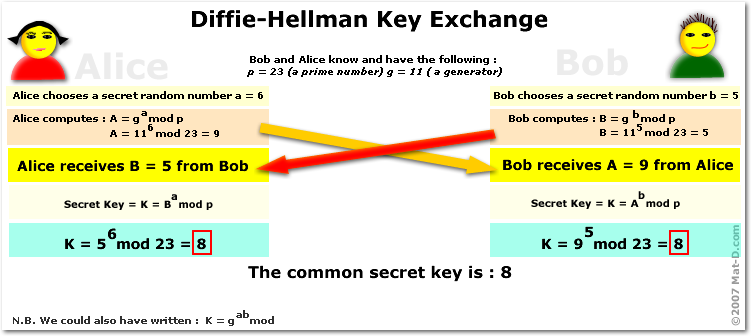
Conceived by Ralph Merkle and named after Whitfield Diffie and Martin Hellman, the Diffie-Hellman key exchange is one of the fundamental tenets of public-key/asymmetric cryptography. Diffie-Hellman is a method of exchanging cryptographic keys over a public channel safely and securely.
Consider the following example.
- Alice and Bob decide to exchange confidential information with each other over a private channel.
- To do so, they have agreed on a public number, 7, which will be known by all the eavesdroppers as well.
- Alice has a private number (10), while Bob also has a private number (5).
- Alice adds her private number to the public number and sends the result (17) over the public network to Bob.
- Bob adds his private number to the public number and sends the result (12) over the public network to Alice.
- Alice again adds her private number with the number she got from Bob and gets 22. Similarly, Bob also receives the same number after adding his private.
- Both Alice and Bob get 22 without having to divulge their private information to the public.
The mathematical form of the Diffie-Hellman exchange
Let’s define some parameters before beginning:
- There is a generator g of a finite field of size n.
- Within that field, we choose two random values a and b.
- Since it’s impossible to determine g^ab, given only g, g^a, and g^b, this becomes a trapdoor function.
Alright, so now that we have defined our parameters, let’s look at the situation that we have at hand:
- Alice chooses a random private number “a” and sends Bob a message M1 such that M1 = g^a mod n.
- Bob chooses a random private number “b” and sends Alice a message M2 such that M2 = g^b mod n.
- Alice gets M2 and uses her “a” to get the special message g^ba mod n. Similarly, Bob gets M1 and adds his “b” to receive the same unique message.
- Both of them end up with the same message “g^ab mod n” without disclosing their secret, private message.
Best asymmetric encryption algorithms
The two most commonly used asymmetric encryption algorithms out there are:
- The Rivest-Shamir-Adleman algorithm aka the RSA
- The Elliptical Curve Cryptography.
#1 RSA algorithm
The RSA algorithm, named after MIT professors Rivest, Shamir, and Adelman, is a widely used asymmetric algorithm. The algorithm was derived directly from the Diffie-Hellman exchange. So, before we understand how it works, let’s look at the parameters in play.
- The secret message that Alice wants to send Bob is “m.”
- We have two randomly selected numbers “e” and “N.”
- We have our ciphertext “c,” such as c = m^e mod N. This equation allows you to trigger trapdoor functionality like this – it’s easy to get “c” if you know the other values. However, it is impossible to derive the other values if you just know “c.”
- Now, when it comes to the decryption process, we need another key. For that, we will choose a random variable “d,” such that c^d mod N = m.
- Since we have already established that c = m^e mod N, we can directly substitute this in the equation above and get -> m = m^ed mod N.
From the final equation, m = m^ed mod N, the values of our public key and private key are:
- Private key = d.
- Public key = e and N.
RSA key: Derivation and generation
The public and private keys can be mathematically derived from each other. This derivation should satisfy the trapdoor function such that its infeasible for anyone to get the public key from the private key. To do this, RSA uses prime factorization.
What is prime factorization?
Every positive integer >1 can be written as a product of prime numbers (or the integer is itself a prime number). Eg. 14 is 7*2, while 256 is 2 * 2 * 2 * 2 * 2 * 2 * 2 * 2.
Keep this in mind, let’s take another look at the ciphertext equation we have derived above -> C= m^e mod N. The number “N,” acts as the trapdoor function here. It is impossible to know the prime factors of N by just looking at it. However, if you know the value of the prime factors, you can easily find N by multiplying them.
To summarize:
- Generate two random prime numbers P1 and P2 and multiply them to get N.
- Keep P1, P2 private and make N public.
- Ensure that the value of P1 and P2 is big enough to make the trapdoor as effective as possible.
So, we have determined “N.” However, we still need to know the values of “e” and “d” to get both the private and public keys.
To get these values, we will be looking into another field of mathematics called “breakability” or phi().
Understanding the phi () function
If N is a random integer, then the output of phi(N) will be the total numbers of integers between 1 and N, which don’t share any common factors with N, except 1.
Let’s take an example. If N = 6. The numbers between 1 and 6 that don’t share a factor, except 1 with 6 are 1 and 5. Since there are only two numbers that don’t share a factor, the value of phi(6) = 2.
There are two interesting observations about the phi() function that you should know:
- The larger the value of N, the more difficult it is to find phi(N).
- If N is a prime number, then it is easy to find phi(N). By definition, the only number a prime has common factors with except 1 is itself. So, the value of phi(N), where N is a prime number, is N-1.
To understand the latter point, let’s take a working example. Suppose we have a prime number 11. The only number between 1 and 11- 1,2,3,4,5,6,7,8,9,10,11 – which has common factors with 11 except 1, is 11. Hence, the value of phi(11) is 11-1, or 10.
Phi functions also happen to be multiplicative. Meaning – phi(A*B) = phi(A) * phi(B). Keep this in mind as we go back to our P1, P2, N.
We know that -> N = P1 * P2
If we phi() both the sides, we get: phi(N) = phi(P1 * P2).
By using the multiplicative property, we get -> phi(N) = phi(P1) * phi(P2).
Since P1 and P2 are both prime numbers, we can also write the above equation as:
phi(N) = (P1-1) * (P2-1).
Trapdoor functionality using phi()
Now, we finally get our trapdoor functionality. Suppose P1 is 13 and P2 is 19. That means N is (13*19 =) 247.
As per the formula -> phi(247) = (13-1) * (19-1) = 216.
If you know the value of a particular number’s prime factors, it becomes very simple to find its phi().
Taking a look at what we have so far:
- We have the modular exponential function (m = m^ed mod N and the rest).
- We have the phi function, notably -> phi(N) = (P1-1) * (P2-1).
Now, to understand the last step of RSA, we need to bring both these aspects together. To do that, let’s look at another theorem that Euler came up with.
For any two random numbers m and N that don’t share a factor:
m ^ phi(N) ≡ 1 mod N
NOTE: The “≡” sign means “is identical to.”
We will bring in a couple of modifications to this equation to make it more harmonious with the equations we already have.
The First Change
We know that 1^k = 1 for all k.
In the equation -> m ^ phi(N) ≡ 1 mod N, we will multiply the LHS with 1^k (it won’t make a difference in the output since 1^k is 1).
1^k * m ^ phi(N) ≡ 1 mod N.
OR
m ^ k*phi(N) ≡ 1 mod N.
The Second Change
We know that for all m, m*1 = m.
Let’s multiply both sides of our modified equation. We will get -> m*m ^ k*phi(N) ≡ m*1 mod N OR m ^ k*phi(N)+1 ≡ m mod N.
Now, let’s compare this with another equation that we derived a little while back:
m ^ e*d mod N = m
Upon comparing the equation, we can see that they are pretty similar. By the process of substitution, we can derive the following conclusion:
e*d = k*phi(N) + 1
OR
d= (k*phi(N) + 1)/e.
Finally, we have an equation that tells us how we can derive our private key (d) from our public keys, e and N.
This is how the RSA algorithm works.
#2 ECC algorithm
What is ECC?
Elliptic-curve cryptography or ECC is a form of public-key cryptography based on the algebraic structure of elliptic curves over finite fields. An elliptical curve is any curve that satisfies the following equation:
y^2 = x^3 + ax + b
Where (x,y) is a variable point on the curve, while a and b are constants.
Mathematical properties of ECC
#1 Addition
NOTE: Image credit for the curves shown below -> CSBreakdown youtube
If you want to add two values V and A, we will trace them on the curve and run a line through them. We will then see where the line intersects the curve.
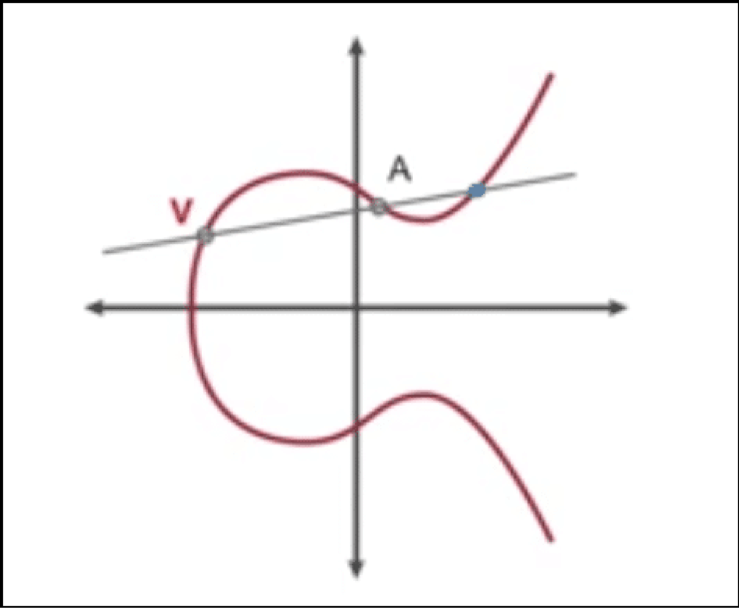
Following that, we draw a vertical line through the point of intersection. The place where the vertical line intersects the curve again is considered the point of addition, aka, V+A.
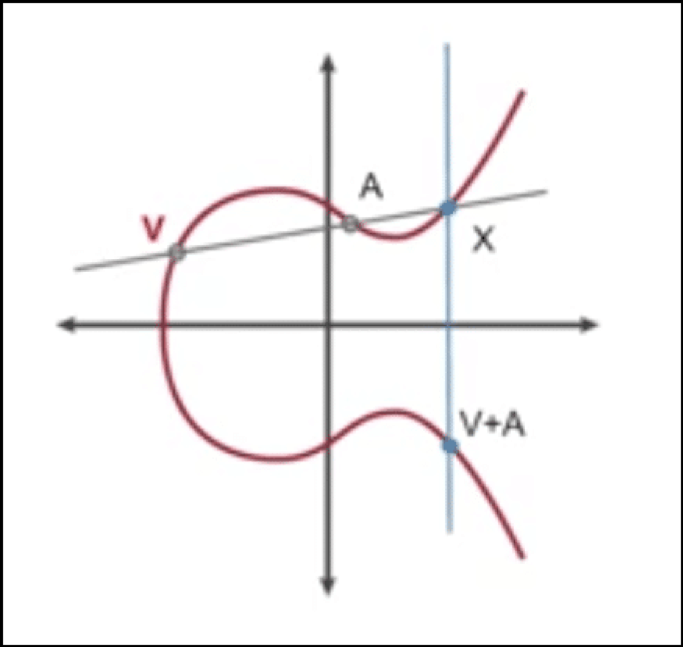
#2 Multiplication
When we multiply a value with an integer, we are adding it with itself a specific number of times. For example, 3*X is X+X+X.
The same logic applies here. We have a value V and if we want to get 2V, we can add V with itself. We do that by drawing a tangent from V and vertically reflecting the point of intersection:
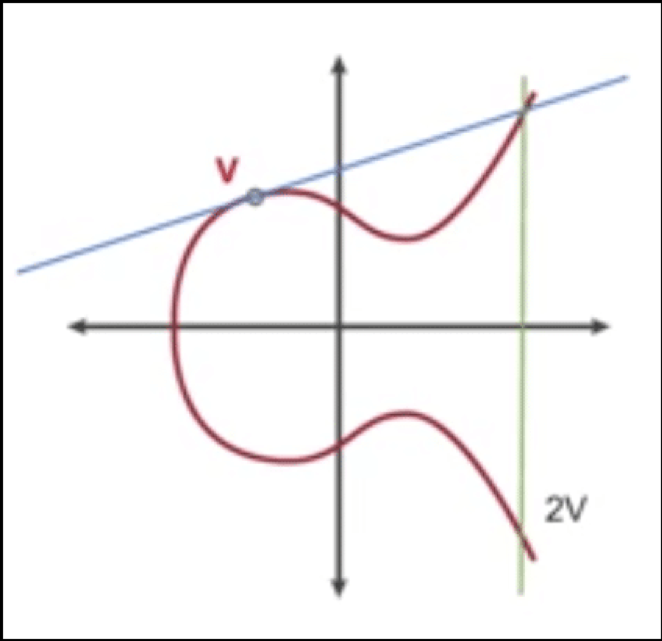
Now, if we need to find 3V, we can simply V and 2V:
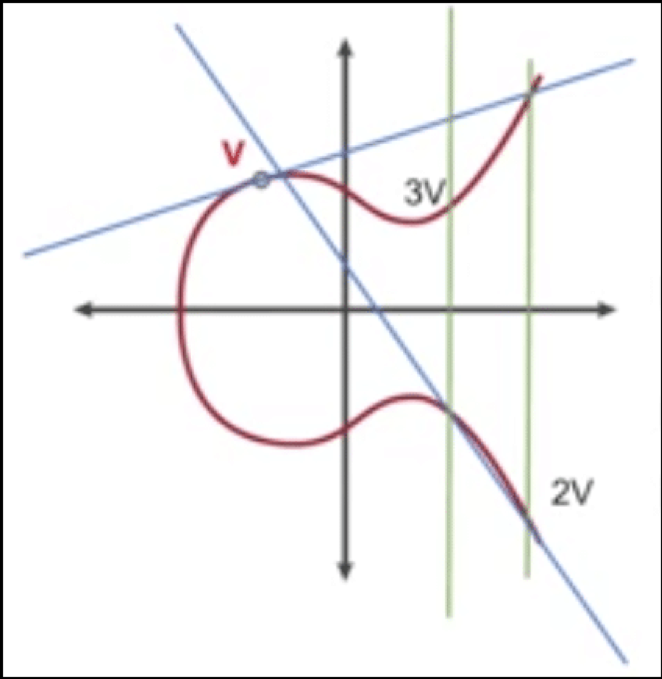
What is ECC: Diffie-Hellman key exchange
Alice and Bob want to exchange messages over a public network without revealing their personal info. This is how it works:
- Both Alice and Bob will agree on the curve to use and select a random point on it.
- Alice has private info “a” and multiplies it with P to send over aP to Bob. Bob has private info “b” and sends over bP to Alice.
- Multiplication is a trapdoor function in elliptical curves since division is infeasible. So, even if P, aP and bP are made public, no one will be able to derive a and b from it.
- Alice will now multiply a again with bP to get abP. Bob will multiply b with aP and get baP. As per the ECC properties, abP = baP.
- Alice and Bob reach the same conclusion without sending over their private info.
- ECC successfully satisfies Diffie-Hellman conditions.
What is ECC: Elliptic curve signature verification
Before we look into the process, let’s declare some values:
- d, the private key.
- z, the message.
- Q, the public key.
- G, a constant point on the graph
- k, a random number generated for each unique signature
- n, another constant value
Phase 1: Signing the message
- The value of your public key Q = dG.
- Multiplying the k with G points to a specific point on the graph (x,y) such that (x,y) = kG.
We will determine two values r and s, which will be the coordinates of our signature.
- r = x mod n.
- s = (z + rd) k^-1 mod n
The sender sends (r,s) to the verifiers for verification.
Phase 2: Message verification
Verification is a straightforward process. The verifiers will execute the following:
z*s^-1*G + r*s^-1*Q
Upon solving, this equation gives the point (x,y)
With the equation r = x mod n, the verifiers can solve for x and see if the values match. If it does, then the signature is valid.
Why Bitcoin opted for ECC over RSA
ECC offers the same level of security as RSA by consuming far fewer bits. Consider the following:
- A 256-bit ECC will provide the same security as 3072-bit RSA.
- A 384-bit ECC will provide the same security as a 7680- bit RSA.
The reason why ECC is so efficient is because of the speed with which it makes mathematical computation. For example, suppose we have a value P and we want to find 100P. Instead of just adding P to itself 100 times, it can do the following:
- P+P = 2P.
- 2P+P = 3P.
- 3P+3P = 6P.
- 6P+6P = 12P.
- 12P+12P = 24P.
- 24P+P = 25P.
- 25P+25P = 50P.
- 50P+50P = 100P
As you can see, a process that should have taken 99 steps took just 8.
Cryptocurrencies and asymmetric key cryptography
The moment you get a Bitcoin wallet, you will receive your public address and private key.
- The public address will be the location where you will receive your Bitcoins.
- You will then use your private key to unlock the bitcoins sent to your wallet..
- When you send someone Bitcoin, you will need to sign it off with your private key to verify the transaction.
How does the Bitcoin wallet generate your public address and private key?
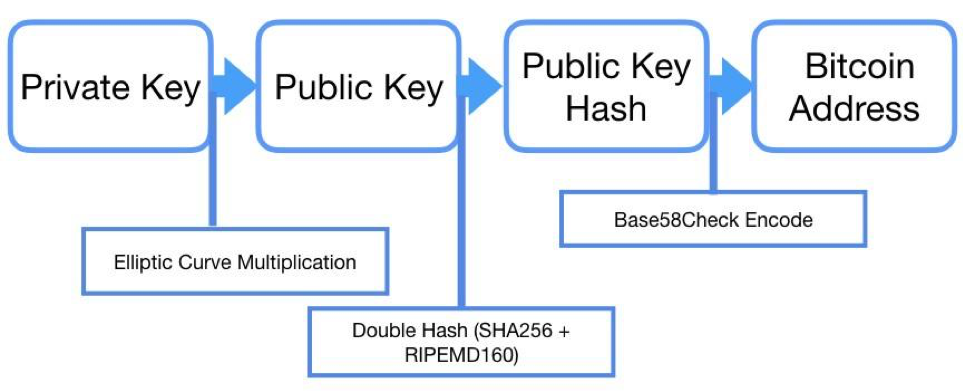
- Your private and public keys are generated via ECC multiplication as described above.
- The public address then passes through SMA -256 to generate a hash.
- That hash then passes through RIPE MD 160, to get shorter hash. We will call this HASH_1.
- HASH_1 gets passed through SHA-256 again to generate another hash. The first 7 bits of this hash becomes HASH_2.
- Bitcoin public address is the combination of HASH_1 and HASH_2.
- It is infeasible to know the value of the private key from the Bitcoin public address.
Asymmetric vs Symmetric Encryption: Conclusion
It is essential that you first have a basic idea of asymmetric cryptography if you want to gain a good understanding of cryptocurrencies. In this guide, we have shown you how different symmetric and symmetric cryptographic processes work. You should now have a better understanding of some of the underlying processes that get triggered when you decide to interact with your cryptocurrencies. With a rising blockchain developer salary curve and decentralized finance (DeFi) on the rise, it is going to be more important than ever with cryptocurrencies and online blockchain schools. If you want to know more about cryptography, be sure to check out Ivan on Tech Academy and its cryptography course!