The blockchain was initially introduced by Satoshi Nakamoto, the inventor of Bitcoin, as a time-chain concept. Bitcoin transactions would be created and validated in a decentralized, peer-to-peer network and stored in a public ledger, which was later called “the blockchain”.
This distributed database where transactions get stored is what Satoshi referred to as time-chain or a chain of time-stamped blocks of transactions.
The most interesting features of blockchain technology are security and decentralization. Simply put, a blockchain allows users to send, receive, and store transactions in a time-stamped, public, open, and permissionless distributed database. These transactions are grouped together in blocks. Since blocks are hashed and linked together in chronological order, to alter the transactions in one block, an attacker would have to alter all subsequent blocks.
Therefore, blockchain technology seems to be an amazing and useful upgrade to distributed ledger technology (DLT). Not only can participants receive and send money directly between themselves, but it is possible to store all sorts of data and information in a blockchain.
In this guide, we will discuss:
how the blockchain fits into the existing data-structures,
what are the key differences between public and private blockchain technology,
what is the relation between blockchain and consensus algorithms,
an introduction to the blockchain trilemma and why the blockchain cannot easily be scaled,
what are some cool applications of the blockchain and,
what does the future hold for blockchain technology?
After reading this guide, you will become an expert on blockchain technology and will understand all the ins and outs of any discussions and debates around the topic.
Ready to dive deep? We sure are!
What is the blockchain?

Ivan on Tech: Good Morning Crypto
Are you looking to learning how Bitcoin has been developing during 2020? If so, you have come to the correct space. To learn more about blockchain development and receive a certification, the best choice is always to use Ivan on Tech Academy.
Moreover, blockchain technology is the #1 skill in LinkedIn‘s latest rating. Because of that, you should definitely learn more about Ethereum to get a full-time position in crypto during 2020.
Now, to the good stuff!
Data structures and the blockchain
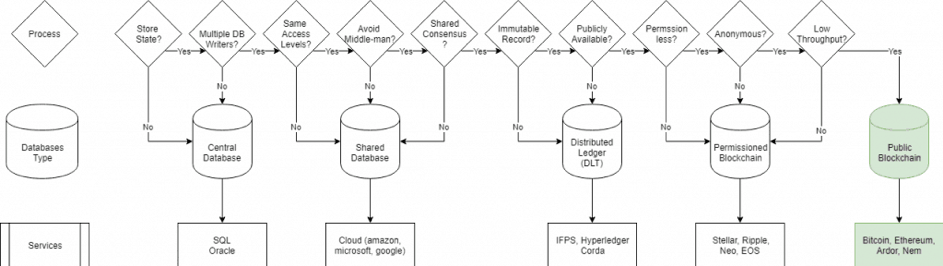
The blockchain exists within a spectrum of data-structures. To make the guide whole, we will first explain what different types of database types exist, what are the most common services available for each, and, finally, we will explain how organizations usually choose between each type of data-structure.
To illustrate the decision-making process, we’ve created the above diagram. It shows what questions are usually asked in order to select the most appropriate database type.
Central databases: the very first type of database that exists, and the most widely used, are centralized databases. This data structure is useful for recordkeeping information in a single database and/or server, and there are multiple access levels that grant access to different parts of the system. These types of databases store all types of information but do not require to store the state of every input and do not require multiple database writers.
Shared databases: when the database is kept within a cloud environment, and there is a requirement to share some of the database information with other services, people, or organizations, it’s useful to have a shared database. Commonly, these types of databases have different access levels for each user group and do not require any type of shared consensus. Since there’s a database administrator, decisions occur from top-bottom.
Distributed Ledger: the next type of database we need to address are distributed ledgers (DLTs). Essentially, a distributed ledger allows many peers to communicate directly since there is a shared consensus on who can write to the database and update records. The information is, however, not publicly available, and the records are not created for immutability, since different types of users may update previous records with new information. Hyperledger and Corda are two of the most widely known and used DLT protocols to date.
Permissioned blockchain: when public blockchains emerged, some of the cryptocurrency projects that sprouted required some or all participants to register an account and still had different access levels. Permissioned or private blockchain allows organizations to control who has access to what data, who can write, update and read records and there usually is a central coordinator. Some great examples to date are Ripple, Stellar, Neo and EOS. While consensus differs from cryptocurrency to cryptocurrency, the common theme is that permissioned blockchain technology helps projects to scale, as decision-making happens from top-bottom. Therefore, the information recorded does not need to reach all peers at the same time, since consensus does not require all participants’ validation.
Public blockchain: the main key differences between public and private blockchain technology relates to both access levels and consensus coordination. In simple terms, a public blockchain is a permissioned and distributed ledger, where any and all participants can record and validate information stored in a public manner. Essentially, anyone can write data by sending a transaction and validate the information by running a full-node that runs the consensus algorithm rules. Due to its decentralized nature, most public blockchains are quite slow and inefficient; however, since information is highly distributed, it is also near impossible to make changes to previously recorded states.
Blockchain technology is the base layer for all crypto transactions. It works as a database which stores them and it exists in the realm of DLTs or distributed ledger technology. Commonly, a blockchain is said to be a DLT; however, a DLT may not be a blockchain, as you can see from the diagram above, discussed in this chapter.
The key differences between DLTs and blockchain technology are based on both the permissions and roles of all participating users. Usually, DLTs have multiple roles linked to different users and groups, much like admins, operators, among others. On the other hand, in public blockchains, participants have the same rights and permissions.
Some great examples of DLTs are Hyperledger and Corda. Now, what is blockchain technology, and why is it so hyped?
Intro to public blockchain technology
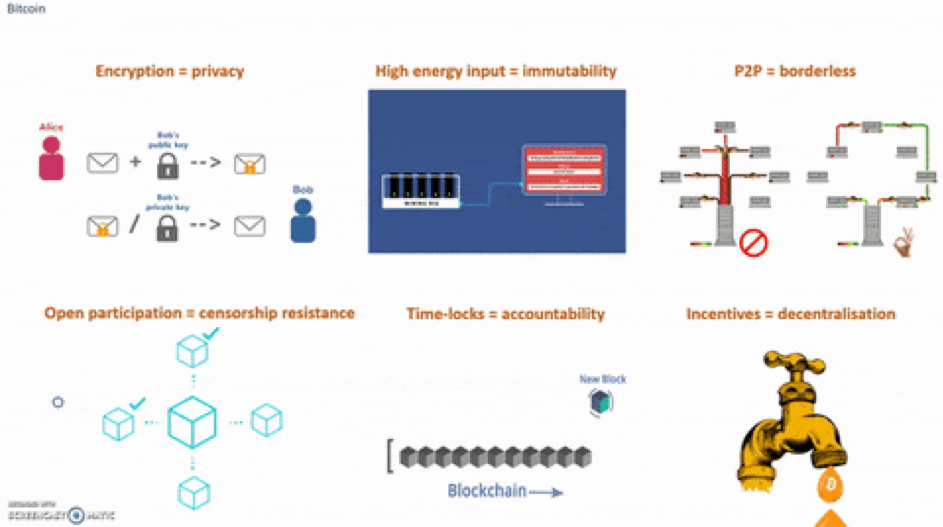
Blockchain technology is a cryptographically secure distributed ledger run by crypto incentives that incentivize nodes operating in the same network, to transact and exchange data in a P2P, decentralized fashion, and to reach consensus on the state of the global network chain. Implementing a distributed and open system, targeting disintermediation, can reduce failures inherent to centralized forces, much like, corruption, lack of transparency, censorship, coercion, transaction costs and excessive market power.
Bitcoin was the first-ever cryptocurrency and was created by Satoshi Nakamoto a person or group of people who remains anonymous, introduced the concept of a blockchain.
When cryptocurrency enthusiasts discuss “the blockchain”, most commonly they refer to public blockchains, where everyone can participate, by validating and posting transactions.
The blockchain data infrastructure is made-of a chain of consequent blocks, stored in blocks within a distributed ledger (distributed database) that contain individual transactions. In terms of infrastructure, most cryptocurrencies present a blockchain infrastructure. Despite that, in terms of governance and who can alter the blockchain state, post-Bitcoin blockchain cryptocurrencies tend to present other degrees of openness.
To better understand public blockchain technology, let’s dive deep into each component that comprises them and makes them whole.
Public blockchain specs
To fully understand how a public blockchain works, one must look into all its moving parts. Essentially, a public blockchain is made of the following pieces:
A public ledger, or database, which is distributed among all participant nodes and where information is written by users posting any transactions. Participants may write to this open database by either sending to or receiving from, a transaction. Addresses are generated via private-public key cryptography, usually pseudo-anonymous, and all recorded information is linked in multiple blocks, all time-stamped by the creator and validator.
PGP encryption, or pretty-good-privacy, which is a technique that creates private-public addresses, based on a hashing algorithm. This technology helps users to prove they are the rightful owners of some data, without revealing their master key (or password). PGP encryption gives users additional privacy to transact independently and in a digital format.
A cryptocurrency, or token, that represents a currency associated with all transactions that occur on a public blockchain. Cryptocurrencies may grant its owners multiple properties, such as voting rights, the right to write on that blockchain, income rights among others. A cryptocurrency can be a digital representation of a currency, a good, a collectible, or mostly any other asset. Cryptocurrencies are key, as they give an incentive for users to keep the network secure. More on that later.
Distributed consensus, most commonly associated with proof-of-work (PoW), or the technology that requires any user to spend energy to resolve complex mathematical computational problems, in order to validate transactions and to keep the network secure. To incentivize network validators to behave according to the protocol rules, and to make the network secured and decentralized, a cryptocurrency is used. The goal of distributed consensus based on PoW, is that by requesting validators to keep spending more and more energy, in order to find the right solution to the computational problem at hand, usually called a hash, it’s possible to maintain the security of such a network by making it near-impossible for anyone to have more than 51% of the total voting power. Thus, the consensus within a network remains decentralized.
A permissionless P2P network, which grants users the right of ownership as they can keep their cryptocurrency in a private address and not depend on third-parties (like banking infrastructure or traditional payment channels). P2P networks, like uTorrent, allows users to share information freely with one another. Within permissionless P2P networks, users who possess the right public-private key pair will be the rightful owner of such piece of data.
Let’s see how the features described above compare between DLTs, permissioned blockchains and public blockchains.
Public vs private blockchain?
Blockchain technology may be the driver for a better web 3.0, however, to accomplish such goal cryptocurrency enthusiasts should focus on permissionless and public technology, rather than private-blockchain use-cases. The reason follows: the future of the web is being built on top of permissionless technology, like Bitcoin and Ethereum. Additionally, when we take into account the most widely adopted operating systems (Linux, Android), software (open street maps, BitTorrent) and platforms (Wikipedia), we notice most are open-source and have open governance models.
Nonetheless, there are many use cases of private blockchains, as we discuss below. To conclude this chapter, we would like to underline the most adopted cryptocurrencies and projects use public blockchain technology, such as Bitcoin and Ethereum.
Intro to private blockchain technology
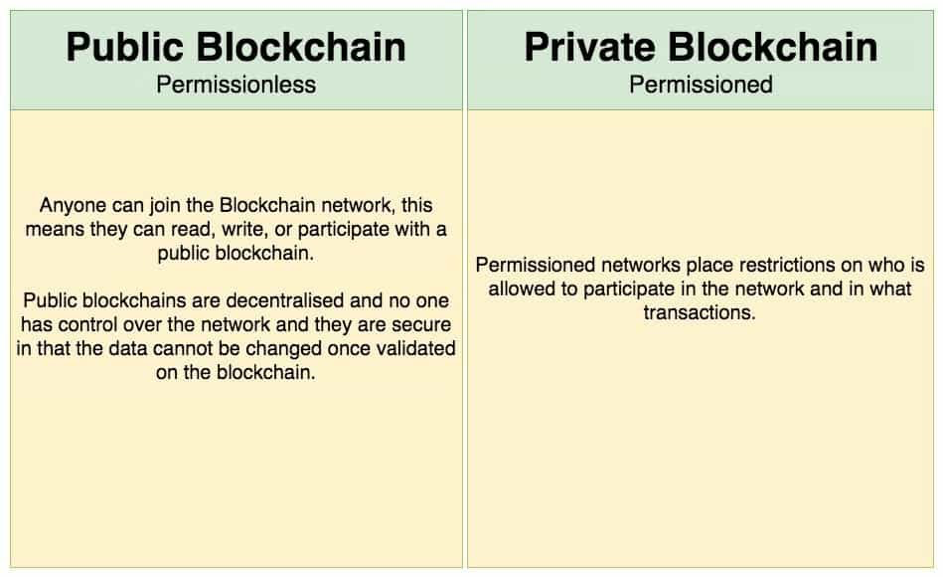
As we’ve discussed above, a public blockchain is a permissionless, P2P, open and distributed blockchain. Anyone who wishes to do so, can join the blockchain network. This means participants can read and write to a public blockchain, without asking for permission. Essentially, there are no restrictions since access levels are the same across all players. Public blockchains are decentralized, as no single entity has control over the network, and they are secure as there’s an extreme cost to changes, once the blockchain validates the data.
At the same time, private blockchains are closed and permissioned blockchains.
Permissioned networks, usually, place restrictions on who is allowed to participate in the network, as a miner or validator, in what transactions and under which conditions. In a nutshell, permissioned blockchain is not decentralized in terms of governance and participation.
Nonetheless, our goal is not to argue for or against private blockchain technology. Being agnostic, means we prefer to follow trends and use all possible technology to the best of our capabilities.
Although the current market has prefered permissionless blockchain, being Bitcoin and Ethereum the most adopted, one cannot argue there is no space for permissioned technology.
In permissioned blockchains there are usually different access levels:
Admins: the group of users who can assign roles to other groups of users. In most cases, admins have the overall control of nodes and participants’ actions (who can write to the blockchain and under what circumstances).
Blockchain writers: the group of participants who can write some information to the blockchain.
Blockchain readers: the group of users who can see some or all information available on the blockchain. Most likely, different groups of blockchain readers will have access to different parts of the network, meaning, information available may depend on the participant.
Most commonly, in permissioned networks the identity of users is known – even though there are a few exceptions.
Permissioned blockchain is important for corporate uses, such as blockchain for the business, or blockchain for supply value chains, because admins know who an individual is, what organization they’re associated with, and what their role is. Therefore, we assume that participants are going to behave fairly because if not, we know exactly who’s misbehaving and they know that they might suffer the consequences for any mischief. Some great examples and use-cases are Ripple and Stellar.
The Blockchain and consensus algorithms
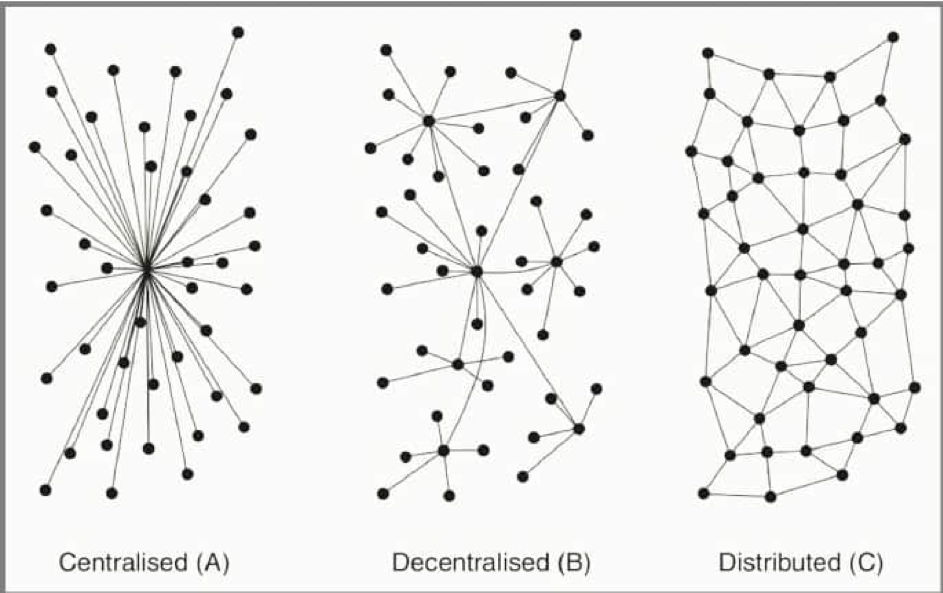
As mentioned in the initial data structures section, proof-of-work (PoW) – or any other distributed consensus algorithm – just plays a part, in a bigger network infrastructure play.
Before diving deep into the “why”, let us explain the image above. While centralized systems have a central point of failure, decentralized systems improve on this bottleneck by having multiple centralized points of failure. However, distributed systems solve this problem by allowing all nodes to have a full copy of the database, which means that upon a failure, recovery becomes much faster and easier to achieve. Therefore, what makes distributed consensus that special is the fact it allows an entire system to fail and fully recover without compromising the entire structure.
Additionally, the reason why distributed consensus is much needed is due to the fact participating agents, commonly, cannot trust each other. Therefore, when should distributed consensus algorithms be considered?
In our opinion, only when all parties want to have the same set of rules for all participants. In other words, when there is an absolute need to have no central authority over the database writers and readers.
If there is a requirement for parties that do not trust each other to trade, a public blockchain can be a terrific solution. Essentially, as we’ve discussed, public blockchain does not require buyers and sellers to trust each other. However, if that is not the case, there are plenty of other infrastructures that can process transactions faster, than public blockchains. When there is a degree of trust among participating agents, private blockchain may be the best use-case, or even a DLT solution may apply.
There are many alternative paths to achieve distributed consensus, either by requiring participants to waste energy to participate (PoW), or by requiring a certain amount of the underlying cryptocurrency as a stake (PoS). Each has its own advantages and bottlenecks, but the overall goal of consensus is to have a set of rules, easy to follow by participants, that helps them write and retrieve information from the global distributed database (or blockchain).
The three main consensus algorithms used in public and private blockchain technology are:
Proof-of-Work, or PoW, where a group of participants has to waste energy (mine) in order to find valid block headers. In turn, after finding a valid block header miners can pick up transactions and add them to a block, which gets validated by other nodes that receive the block information after it is created by the initial validator. PoW is known to be a probabilistic consensus mechanism, since it’s never 100% certain a block of transactions will be finalized. What this means is that, given enough energy inputs, it’s possible to alter a block and subsequent blocks – even if in reality that outcome would require massive amounts of energy, which makes it infeasible. Bitcoin is the most widely adopted PoW-based cryptocurrency, followed by Ethereum.
Proof-of-Stake, or PoS, where participants have to lock a stake in the network’s native cryptocurrency, in order to create and validate blocks of transactions. Unlike PoW, PoS has finality, which means after a block of transactions is created it can never be changed. However, since there are no energy requirements, and the only thing a validator might lose by tempering with the network is the active stake, it means once a validator possesses over 51% of the validating power, it’s near impossible to change it. Therefore, the lack of an energy input might make PoS great for decentralization but weak in long-term security. Great examples of PoS cryptocurrencies are Ardor and Dash. Ethereum will soon move into the PoS category as well.
Delegated Byzantine Fault-Tolerance, or dBFT, is a consensus mechanism which assumes some degrees of censorship. This is, not all parties have the same access levels. While some validators can write transactions to the blockchain, most can only read the information. While dBFT is brilliant for scalability, it’s quite weak in terms of security (single-point of failure) and decentralization. Some examples of cryptocurrencies using versions of the dBFT consensus algorithm are Neo, Ripple and Stellar.
To fully understand how each consensus algorithm fares in terms of security, decentralization and scalability, one should look into the “blockchain trilemma”. In other words, how do each consensus algorithm contribute to the overall security, decentralization or scalability of a certain network?
Is PoW the best algorithm to maintain long-term security, decentralization and scalability? Or, perhaps, other alternative consensus algorithms like proof-of-stake (PoS) or delegated byzantine fault-tolerance (dBFT) could do the trick?
Let’s find out.
The Blockchain trilemma explained
The blockchain trilemma was initially introduced by Vitalik Buterin. It refers to the accepted idea that it isn’t possible, network-wise, to scale a public blockchain without compromising either decentralization, security, or both.
A similar problem takes place in Computer Science (CS) space, and has been openly discussed since the early 1980s. It’s generally known as the CAP theorem and it underlines that in a decentralized and P2P data storage system, it is near-impossible to have more than two out of the three properties we discuss below:
Partition tolerance: The ability for a system to continue to function even if network nodes drop or delay them.
Consistency: The ability for every read to receive the most recent write, or an error.
Availability: The capacity for a system to receive a request (non-error) response, without the ultimate guarantee that such a message contains the most recent write to the database.
Before we dive deep into where each cryptocurrency sits in the trilemma spectrum, let us give you a brief overview of the three components that make up the “public blockchain trilemma”.
Decentralization
Decentralization refers to the ability for participants to exchange information (transactions) without a central authority controlling the network. In other words, decentralization vouches for censorship-resistance, as there is no authority nor a single point-of-failure.
In order to reach a much higher level of decentralization, multiple roles need to work together, within any given crypto protocol.
The three roles we mention are the users, who wish to post a transaction; the validators, who record and then verify transactions obeying to certain protocol rules; and the programmers, who suggest amends to the code, maintain the code, and vote on new features, defining the future directions of the cryptocurrency project.
The further decentralized a network is, the more difficult it is for a single agent to control the network, to make changes to previous transactions, or even to take it down. Additionally, higher decentralization means an increasing number of participants, since there is no authorization required to join. Plus, the higher the number of participants, the more robust a system is in terms of security and fault-tolerance.
Speaking of the devil, allow me to dive into another important dimension – namely security.
Security
In order for a cryptocurrency protocol to be fully secure, it needs to be both resilient in short term and immutable in the long term. What we mean by resilience is the capacity for the protocol to be able to prevent and/or recover from short-term attacks. Immutability in the long term happens when it’s impossible to make changes to previous states of the blockchain.
Yet another feature that plays a major part in security, protecting a protocol from spam or sybil attacks, is throughput, defined by the number of transactions per second, or TPS. In essence, since most public blockchains are asynchronous, users do not need to be online when a transaction happens, nor nodes need to be online all the time in order for the information to propagate correctly. When we discuss the importance of TPS in asynchronous networks, we should explain that the lower the TPS the higher the probabilities there won’t be a conflicting event, since less data is being propagated every second. High TPS in public blockchain may lead to conflicting information being propagated and nodes not being able to cope with the amount of data being processed.
Adding to the above, the propagation delay, or time-lapse (known as network latency), may increase the probability of orphaned blocks. These blocks contain transactions that belong to a dropped chain. Therefore, attacks may take place which target to alter the value of time stamped transactions. To conclude, the higher the throughput, or TPS, the higher the propagation delay between nodes, which increases the surface for attacks.
Logically, since resilience is lower, the security of the protocol diminishes.
As an example let us state the case of Bitcoin – the most secure and decentralized cryptocurrency at the time of writing. It has an incredibly low throughput, and processes only seven transactions per second (TPS) on average. In comparison, PayPal handles roughly 500 transactions per second, and Visa handles a whopping 4,000 transactions per second (TPS).
However, Bitcoin is not only what’s known as a payment layer, but also a store-of-value layer, which we’ll discuss shortly.
Now, let us dive to our final chapter in this “how to scale the blockchain” section, which is scalability and why it matters in the long-term.
Scalability
Scalability is the capability of a network to handle a growing number of transactions. Moreso, it denotes the networks potential to grow in order to accommodate higher TPS numbers. For instance, we consider a system to be scalable if it’s capable of augmenting its aggregate output and be put under greater load, as additional resources – like nodes or validators – are added.
The number of transactions per block is known as the block height. TPS and transaction size are determinant factors for scalability, as well as the network’s decentralization and security. The greater the TPS number and the higher the block number, the higher is the potential of the protocol to accommodate a larger and growing number of transactions, without compromising user experience. On the other hand, faster block times, defined by the time interval between two blocks being approved and hashed together, mean nodes are less fault-tolerant. Essentially, higher throughput always leads to a higher probability of failure between nodes. Hence, the most common solution to accomodate a higher TPS, is to centralize governance, adding a degree of entropy. When a company offers a scalable business model, scalable product or has scalable costs, scalability can be found. Additionally this could be thought to corresponds to potential for growth to those using the network. Scalability augments the capacity for a company to offer additional services, at a cost.
To make the concept far more understandable, we’ve devised the below picture, which details where different cryptocurrencies sit in the decentralization-security-scalability spectrum. For instance, Bitcoin and Ethereum forego scalability in order to make a network as secure as possible. However, these two networks are far from as scalable as Stellar, Ripple or Neo. That is because these two projects choose to forego decentralization to add scaling capabilities, like higher throughput.
On the other hand, we have Dash, or Ardor, that are projects which focus largely on solutions that are scalable. Of course, these are less secure (long-term) than Bitcoin, given they require much less energy, or none, to maintain security.
Let us make our point clear: we cannot have a project that fulfills all needs, in terms of high security, high decentralization and high scalability. All protocols chose ⅔.
Nonetheless, cryptocurrencies have opened the door to completely new distributed consensus algorithms, that one day might crack the blockchain trilemma, even if we need to look into additional layers of complexity.
For example, second-layer solutions could be the answer, since they provide a simple solution that keeps the base layer as secure and decentralized as possible, but are capable of adding extra throughput to the network. We’ll discuss some pretty cool solutions being developed, during the next chapter.
Let’s, yet again, dive deep!
How to scale the blockchain?
The scalability problem, within open-networks, is not something new to practitioners.
What infrastructure, networking, and other CS experts have found is that some problems are technically impossible to solve in a simple way. In a peer-to-peer (P2P) network, due to constraints relating to routing, liveliness and fault-tolerance, one cannot just look to scale a network by introducing more nodes, or by speeding up communication between nodes.
The problem at hand is quite straightforward. As public networks should all be asynchronous and fault-tolerant, there is a limit on the speed of communications. This is done to to maintain the decentralization and security of the network. Essentially, we need to give nodes the time to “breath”.
Communication between different nodes, which is known as network latency, can become slow. This happens when nodes choose to randomly disconnect at any point without consequences. Adding to that, network bandwidth plays an important role in the overall performance of the system, which can be a very impactful problem for cryptocurrency projects, as a great number of people in the world simply don’t have enough resources to purchase large amounts of data, per second.
Let us give an example backed by the communications industry, commonly known as the “last mile” problem. The issue is described as follows. The last mile is typically the largest bottleneck for communication networks. Essentially, the network’s bandwidth effectively limits the bandwidth of data that the customer receives. Moreover, it’s easy to upgrade at the center of the network, but hard to upgrade on far-away layers.
Hence, it’s fairly straightforward to understand the lack of scalability around public blockchain technology – one either vouches for long-term security and decentralization, or for scalability and security, as explained and discussed during the previous chapter.
There are a few technologies and additional protocol enhancements, which can help public blockchains to scale. We shall now go through some of the most vital and interesting ones under development right now.
Before we dig deep, we should underline that the most pressing problem is neither with storage nor CPU processing. Instead, this issue comes from network latency and bandwidth. Ostensibly, the can be understood when nodes take too long to communicate data between themselves. At this point, the network runs the risk of reaching network asynchronousity, destroying the value of verifications. Countless developers and educators tirelessly work towards deploying new technologies for and around blockchains. This is meant to help reduce bottlenecks relating to the network’s latency and bandwidth. Let’s analyze the most important ones:
Sidechains
Sidechains are separate blockchains that attach to its parent blockchains using what’s known as a “two-way peg”. This two-way peg allows “interchangeability” of various assets at a specific rate between a parent blockchain and its sidechain. The original blockchain is usually known as the ‘main chain’ and all additional blockchains to this are ‘sidechains’.
A user on a parent chain firstly has to transfer their coins to an output address. This locks the coins so the user is unable to spend them anywhere else. Once the transaction is complete, a confirmation is sent across the chains. This includes a waiting period, in order for an extra layer of security. After a set waiting period, the corresponding number of coins releases on the relevant sidechain, allowing the user full access to spend them there if he or she chooses. Furthermore, a reverse course of action takes place when funds move back from one of these sidechain onto the main chain.
These sidechains may also require extra communication between chains. Additionally, they also promote higher levels of interoperability between blockchains, which constitutes a vital part of network scaling.
Childchains
While sidechains refer to blockchains which are interoperable and connected to a third-party blockchain (like Loom and POA are connected to Ethereum), childchains refer to a technology that allows for certain transactions to be forged in a subset chain, within the main parent blockchain (like Ardor).
Transactions validated in a childchain are processed and secured by the parent chain forgers.
In essence, childchains help with cross-communication between chains, as all information is kept within the same system; childchains do seem to increase security as there are fewer steps for information to reach the mainchain (parentchain). Nevertheless, if information is stored in the same blockchain, how can such a system improve scalability, when compared to partitioned systems like the upcoming Ethereum Beaconchain, which will bring PoS to Ethereum? That’s a question we’re still looking to answer in the future.
Payment channels
Payment channels constitute an innovation which allows for off-chain state channels to open peer-to-peer (P2P). Essentially, this allows for various users to transact with eachother without paying fees.
The general idea behind this is that you can commit some Bitcoin to open a channel with another node. Consequently, this allows you to transact with said node until the channel closes and the balance releases between participants.
The Lightning Network, which is a payment channel made for Bitcoin, was successfully launched thanks to Lightning Labs and already has more than 2,000 active nodes and about 15,000 channels.
In Ethereum, there’s a similar implementation called Plasma, which is a technique for conducting off-chain transactions while relying on the underlying Ethereum blockchain to ground its security.
Think of Plasma a hierarchical tree of side chains that periodically transfers information back to the main-chain. Ethereum will continue to handle smart contracts in a similar way to how they are handled currently, except it will only broadcast completed transactions to the public Ethereum chain. Plasma takes the concept of off-chain payment channels to the next level, by allowing for the creation of child blockchains attached to the main Ethereum blockchain. These childchains can even spawn their own childchains, which can themselves have another set of childchains – and so on.
Therefore, payment channels – like Plasma or the Lightning Network – can potentially bring together off-chain payment channels with sidechains technology.
Database sharding
The technique known as sharding separates a single blockchain into multiple smaller blockchains that are known as shards. Moreover, each shard is independent and prepares each own transactions. What’s more, some improvements are already under development. This include cross-sharding, which allows shards to communicate between themselves. Put simply, some of the most glaring benefits of sharding are various reduction of total blockchain size. Moreover, this also includes the possibility for a quadratic network performance enhancement.
There are multiple versions of sharding currently being implemented, being the most widely known Near protocol, Polkadot and Ethereum’s Beacon chain. As of early 2020, there are 2 major versions of Sharding in use:
Partitioned sharding, where shards do not communicate with each other directly through a central relay.
State sharding, where shards communicate with each other through a state, or central, relay.
Alternative consensus mechanics
Implementing consensus mechanics that differ from PoW, where miners need to verify the entire blockchain state by committing work through computer power and energy spending, blockchains could potentially become more scalable.
Some of the proposed solutions are represented by either a less decentralized or less secure consensus mechanics. Furthermore, this is done by lowering the overall network security or user privacy, it’s possible to increase scalability.
Such mechanics are associated with PoS or federated systems, like dBFT, as we’ve explained in the previous chapter. Now, let’s analyze what the best use-cases of blockchain technology might be.
Best applications of the blockchain technology
At the moment of writing, the major use-cases for cryptocurrency continue to exist within the monetary and financial realms.
Looking at the image above which shows how each cryptocurrency fares in terms of on-chain volume, we can quickly conclude the monetary and payments use-case is no longer the only viable option for investors and traders.
Firstly, we notice the blockchain infrastructure + stablecoin purposes have clearly surpassed both cryptocurrency and payments. Traders and investors seem to be inclined to multiple use-cases rising from the blockchain technology.
In this chapter we explore what are the most promising fields to explore, why and which cryptocurrency is making the best efforts to improve the field.
We’ll start by discussing the most common use-cases, to the most uncommon ones.
Currency and Payments
The global payments sector is costly, prone to many human errors and quite open to money laundering and other financial schemes. Adding to that, it takes days, if not longer, for currency to cross the world. Additionally, fees are quite substantial for a service that only requires bits to be changed within a database. Blockchain solutions are providing solutions to various remittance companies, including Align Commerce, Abra or Bitspark that offer end-to-end blockchain powered remittance services. For instance, in 2018, Santander merged blockchain to a payments app, enabling customers to make international payments 24 hours a day, while clearing on the following day, becoming one of the first financial institutions providing such a service. Known as “Santander One Pay FX,” the service uses Ripple’s xCurrent to enable customers to make same-day or next-day international money transfers.
Additionally, one can use public-blockchain as a fast settlement’s layer, meaning, crypto-enthusiasts may choose to use, for example, Bitcoin to settle important payments and to store-value in the long-term, while using other cryptocurrencies like Litecoin, Bitcoin Cash, etc, to make fast payments across borders.
Financial Services and Assets
Traditional financial systems tend to be slow, error-prone and cumbersome. Intermediaries often need to mediate the process and resolve conflicts between parties, which adds a layer of complexity and extra-time. Naturally, these processes cost money. In contrast, cryptocurrency users find the blockchain technology quite fast and secure, when compared to the traditional banking system – which takes days to settle global transactions.
Some wonder that a growing number of financial services are using this system to introduce innovations, such as decentralized finance and smart contracts. The former connects lenders with borrowers without intermediaries, through different open-source protocols, or smart contracts, with impeccable system design to allow incentives to run the network and to narrow the behavior of users. Moreover, the latter of these include digital contracts which self-execute and self-maintain when terms are met. As such, they can be used for a plurality of innovations we’ll discuss below.
Funding
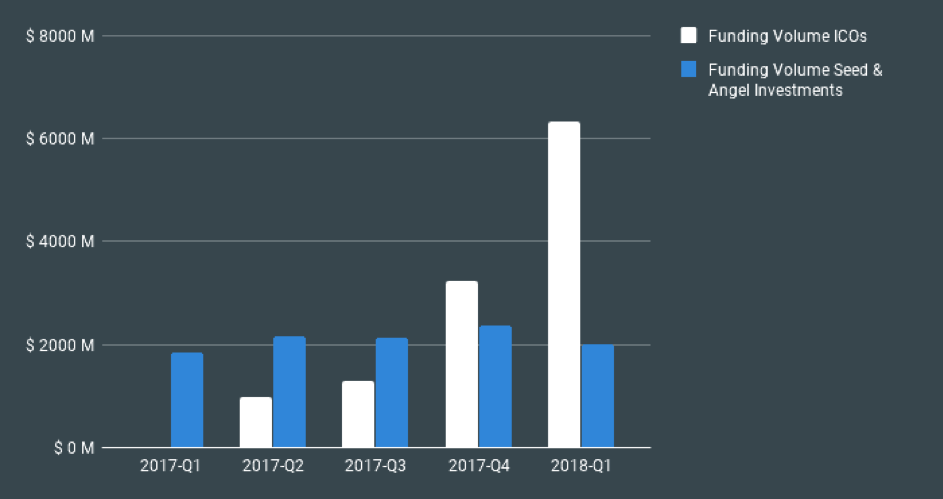
As we saw during the 2017 bull-market, which took Bitcoin close to $20,000 in some exchanges, one of the most widely adopted use-case were initial coin offerings, or ICOs. During this period, throughout 2018, funding for cryptocurrency-projects went from below $2 billion in early 2017, to over $6 billion in early 2018. During the same time, funding volume from Seed and Angel Investments was around $2 billion. This means ICOs had three times the volume of traditional finance. How about them apples, right?
We believe the trend will surely continue in the future, however, what we expect is better projects to surface and obtain a larger market-share of funding, with the development of equity-token offerings, (STOs) and other dividend-payment tokens which will financially reward its token-holders. A great example is Nexus.
To conclude, although ICOs and STOs are a great way to finance teams and projects, it does bring some additional risk. There’s plenty of examples of projects that were just scams, like Bitconnect, or that failed miserably to deliver upon their promises, due to funds mismanagement such as it happened with IOTA.
A brilliant workaround being implemented is quadratic funding. Essentially, it allows token holders to express their preferences when funding or voting, by adding quadratic cost to the operation, where the more funds one receives, the more expensive it is and/or, the more power token holders can exert over the fund holders. Another option is to use a DAO, or Decentralized Autonomous Organization, which creates a mechanism to fund projects based on goals and milestones. An awesome implementation of this process is GitCoin, which opens funding to a completely new range of options.
Borrowing and Lending
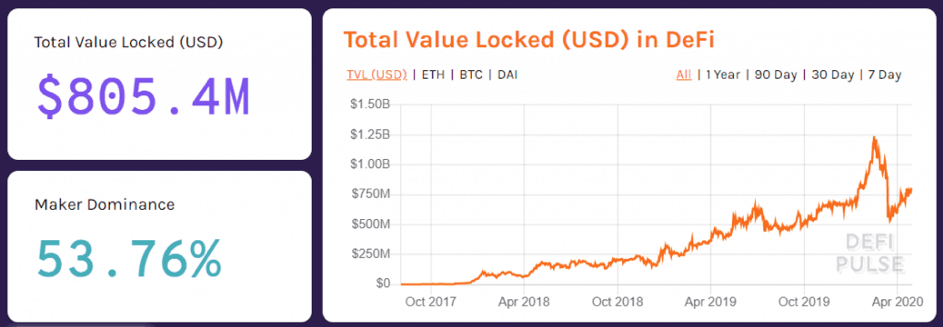
Decentralized borrowing and lending fall under the decentralized finance (DeFi) spectrum. Essentially, through open-source protocols such as MakerDAO, Compound, or Synthetix, it’s possible for users to borrow against their cryptocurrency, namely Ethereum, and to bet on derivatives of certain cryptocurrencies as well. The chart above clearly shows the DeFi space went from near $0, in late 2017, to a top of $1.25 billion in late 2019. At the moment of writing, there’s over $800 million locked in the DeFi space, mostly in DAI and Compound.
Let us explain how these decentralized finance protocols help users.
While Maker and DAI help users to borrow and lend their ETH, through the use of stablecoins and other mechanisms, Synthetix is a derivatives protocol where users can leverage their ETH to bet on the price of other assets.
Not only that, but DeFi gave birth to completely new models such as Flash Loans, where users can borrow up to millions of dollars in ETH and execute operations within the same transaction. What this means is that if users succeed, then the transaction will happen, if users fail the transaction won’t take place since the user won’t be able to cover the cost of borrowing + fees + interest.
Exchanges
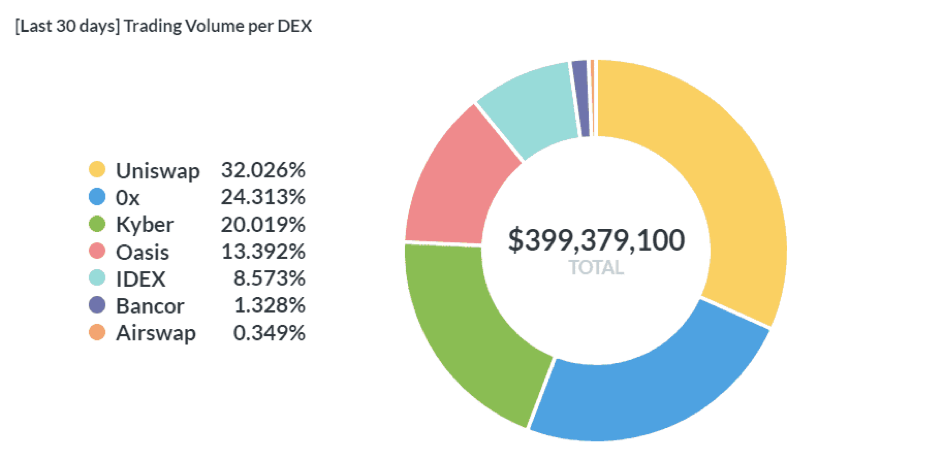
One of the coolest developments in open finance are decentralized exchanges, or DEXs. The key difference between traditional exchanges such as Coinbase or Kraken, is the fact DEXs give users total control over their funds.
Essentially, when you transact in DEXs, such as Uniswap, 0x or Kyber, what these services provide are liquidity pools – created both by users and the underlying protocol – which allows anyone to participate in transacting or by providing liquidity to the system, and be incentivized to do it.
The truly amazing advancement here is that these types of exchanges are not required to follow KYC/AML regulations since users are the ones controlling their assets. The exchange is simply an interface to allow users to easily communicate with a blockchain, such as Ethereum.
To conclude, when using a decentralized exchange users are the owners of their private keys and only they have the control over their assets.
Ownership
Another absolutely incredible functionality of public-blockchain technology is for non-fungible tokens, or NFTs for short. What NFTs create is, essentially, tokens which can hold different characteristics from each other. This type of tokens, built with a plurality of ERC standards, such as ERC-1155 and ERC-721, are key for gaming as they allow users to own and track tokens which have minor differences between themselves.
Do any of you remember CryptoKitties, developed by Dapper Labs? Those types of collectibles are NFTs. What they do is they allow the creator to input specific features to a token, or smart-contract, that makes the asset different from other assets built in the same protocol and system. For instance, in CryptoKitties each cat had different stats and features from each other, which obviously influences the price.
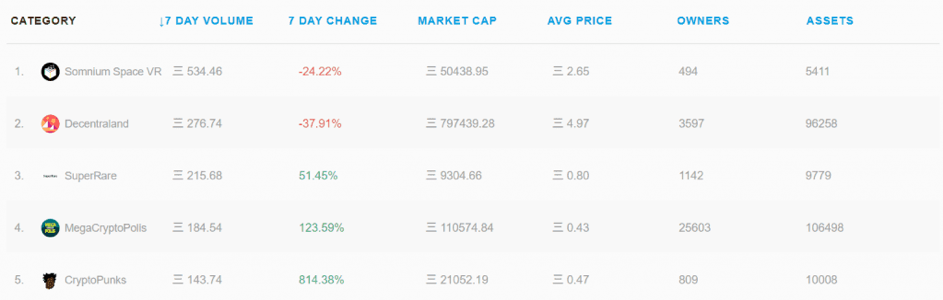
But not only that, other projects have built upon this NFT layer. Looking above, at OpenSea, an open-source marketplace protocol for NFTs, we can see the top three projects already transact substantial sums, between ETH 215 and ETH 500. While Somnium Space VR and Decentraland entitle users to own a piece of virtual land and to build anything they want, SuperRare bundles collectibles and NFTs.
The really cool feature about NFTs is that price varies a lot, much like it happens with traditional collectibles. These tokens are normally quite limited in supply, and each token holds different characteristics from each other, even though they’re built in the same network with the same standards. NFTs are associated with addresses which can be held by users directly. Hence, it’s easy to enforce property rights since the assets live in an address ultimately controlled by the user.
Oracles
One of the most important developments around blockchain technology are open-source and decentralized oracles. Simply put, oracles are pieces of code that are gateways for smart contracts to interact with off-chain applications, whilst limiting reliance on a single source of truths.
Allowing smart contracts to take inputs from outside its blockchain is a double-edged sword; on one hand, it increases the use cases exponentially by allowing interactions with the external world, but it also introduces an element of trust. The miners and validators on a permissionless blockchain cannot deterministically verify all external inputs, and will, therefore, allow execution of anything which matches the predefined criteria of the smart contract.
Essentially, decentralized oracles collect information from multiple sources and aim at possessing the most reliable data. Oracles may be quite useful for applications relying on prediction markets, such as Augur, shipment, and tracking of goods and services, such as FOAM, financial and price data feeds, such as ChainLink – a company already partnered with Microsoft – or even stablecoins price data, such as MakerDAO.
The reason why decentralized oracles work is due to the incentives mechanism built-in. If a source fails to provide reliable information, the stake may be lost, which creates an incentive for accurate data feeds.
Governance
Moreover, one also has to turn to governance-focused applications of blockchain technology. There are three main areas we would like to bring your attention to, from identity and open-governance, to supply-chain products tracking.
Essentially, blockchain may help with decentralized governance models since it adds a layer of incentives and reputation, which when combined make powerful tools for on-chain decision-making.
Let us dive into each category.
Identity
Companies can use blockchain identity management systems to eradicate current identity issues such as inaccessibility, data insecurity and fraudulent identities. There are a few comprehensive services operating in this space such as Namecoin, NameBase and uPort.
Namecoin was the first protocol fork of Bitcoin and was the underlying blockchain for Dot-Bit, the first real-case implementation of a decentralized DNS. Quite impressive if you ask us. In essence, Dot-Bit works by letting users forward their current domains to .bit addresses.
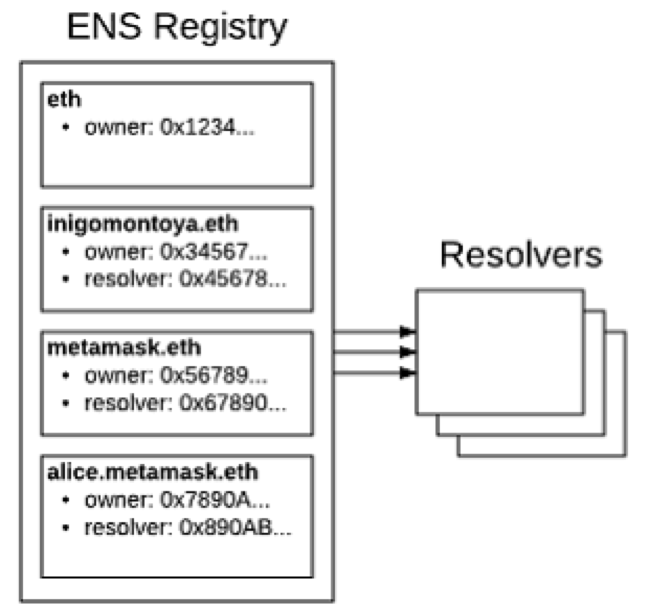
Many interesting projects and products have surfaced since the introduction of Namecoin. Looking at the image above we see how the Ethereum Name Service works. ENS is a DNS, or Domain Name Service, especially built for the Ethereum protocol that is simultaneously decentralized and secure. A smart contract serves as the registrar that manages and updates Ethereum names, instead of using a centralized service like GoDaddy. Anyone can create a human-readable .eth subdomain, and the ENS resolver acts as a translator that converts names to addresses.
Two applications that are built over Ethereum and seem to be getting a lot of traction are Unstoppable Domains and uPort. While the first is an open-source domain service name (.zil, .crypto) which allows anyone to quickly deploy a name and/or domain which works cross-blockchain (Ethereum, Bitcoin, Zilliqa, etc), the second allows user to have an open-source tool to manage their identities over the Ethereum blockchain.
Permissioned ledgers, such as Hyperledger or Corda are also developing solutions targeting identity, which can be quite useful to connect permissioned with public blockchain name spaces.
Open-governance
As we’ve discussed in previous chapters, decentralized technologies give users unparalleled power to transact and interact with a level of security and openness, never seen before. Thanks to cryptography and economic incentives, as we’ve discussed in the first chapters, users can now own truly sovereign assets and build truly sovereign and independent identities, requiring permission from no one. Decentralized and open-source technologies, like Ethereum, solidify freedoms that cannot be taken away, not even by actors with sizable resources. This massive shift in technology requires a new method for organizing these independent individuals: decentralized organizations.
Employing blockchain technology and using smart contracts allow us to create fully decentralized organizations, which are truly autonomous and unstoppable. Are you wondering why these new flat and open organizations matter?
Decentralized organizations change our relationship with governance: from something that is imposed upon us by others, into something we choose to opt into. Open organizations represent something we are equally serving and served, rather than just serving.
Adding to that, with the development of projects such as Aragon, people can coordinate activities and reward organization members through tokens and incentives.
Another cool example is Bityond, a recruitment and talent management engine. Whereas most projects simply assign tokens as a representation of equity, with voting power, Bityond takes coordination one step further: it allocates tokens to users, based on their activities online – inside the platform – and then token holders have not only the power to vote on new platform features, updates and so on, but token holders also have to actually burn tokens for their voice to be heard. Bityond, essentially, adds a cost to governance – much like electricity adds a cost to mining.
Supply-chain tracking
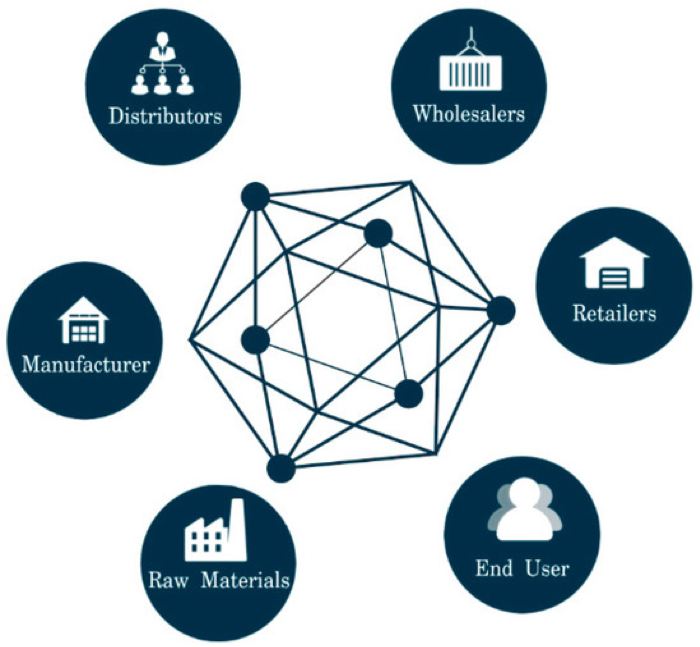
Blockchain provides an achievable use case of the disintermediation of business processes via a distributed information ledger. Blockchain not only facilitates the sharing of multiple tracking information data-sources, but also promotes a network for multilateral open collaboration among supply chain key players. The reason why blockchain may considerably improve the supply chain space, is due to the hunt for transparency and accountability across supply chain processes. These can potentially influence automation and decentralization.
Additionally, with the integration of smart-contracts, it is possible to achieve high levels of disintermediation and solve ongoing issues, such as with the Project Bank Accounts (PBA), where some of the participating agents (companies) withhold payments from suppliers (employees), creating an empty space of financial freedom.
Not only that, but consumers can benefit as well. Even though registering assets or products in a private/public blockchain may have bottlenecks – mostly associated with the social consensus and trust on the entity making the registration of any given product in a blockchain – it’s much easier to prove the source of the goods. If a blockchain is tempered with, it’s also quite straightforward to prove where the tempering happened.
We’ve identified the main three advantages of using a blockchain, for supply-chains:
Increased speed in how money goes from the contract creator to the executor.
Increased transparency in the entire money allocation process, from start to completion.
And, increased accountability, as transactions and steps could easily be verified by any of the participants.
Previous research, performed by Deloitte, a renowned consultancy, has found that in many organizations, procurement costs are a big part of the total cost. For example, about 60% of the cost of a car is attributed to procurement costs. Not only that, but English auctions, Dutch auctions, and sealed bid contracts are well understood, widely used economic mechanisms in the procurement context. This is crucial for supply-chains since it is possible to build decentralized auction systems with blockchain technology – which can definitely reduce the cost of procurement.
To conclude this chapter, we want to underline some important and real-world examples of blockchain for supply-chain, which are laid out below:
Tael (Wabi token): with the Wabi token and Tael’s tracking technology, consumers scan NFC labels to verify product authenticity on every product in the Tael marketplace, as they’re protected with an NFC label. Consumers securely verify product authenticity with their mobile phones. The token has been built over Ethereum.
Modum (MOD token): Modum offers next-generation solutions for supply-chain automation and intelligence solutions. Moreover, they create digital ecosystems that employ Internet-of-Things sensing technology. What’s more, they use blockchain networks and artificial intelligence for a wide range of applications that relate to sensitive goods in various industries. Currently, the company is mostly targeting the pharmaceutical industry. Furthermore, Modum works with with global technology partners including SAP and AWS. In addition to this, the company also has business partners such as Swiss Post and Deloitte. This is means to ensure solutions are fit-for-purpose and that they meet market needs. Additionally, this is meant to ensure quality standards within the company remain high. Modum’s quality management system also has a ISO 9001:2015 certification.
Dorae: partnered with Microsoft, this private-blockchain project digitizes trade documents and automates document processes. Doing so can save users potentially days of waiting time and reducing transaction errors. Additionally, Dorae secures key data on its private distributed ledger system each time a unit material is processed or changes hands enabling traceability and audit. The first use case has been improving the mining processes accountability and transparency (such as the process of mining diamonds). The blockchain used by Dorae is Quorum, a private version of Ethereum.
Hyperledger Fabric: By using IBM’s Hyperleger Fabric blockchain technology, Walmart can now trace the origin of over 25 products from 5 different suppliers. This company intends to roll out its system for more products and categories in the coming months and years. In fact, it recently said that it will start requiring all of its suppliers of fresh leafy greens (like salad and spinach) to trace their products using the system.
Hyperledger Sawtooth: this blockchain-based technology, Sawtooth, records the journey of assets from their point of origin to the last point of delivery. As a real-world use case, Sawtooth has been used to track seafood, from the ocean to the table. IoT sensors attach to any objects sent to someone else for transport. This means it has trackable ownership, possession, and telemetry parameters including location, temperature, humidity, motion, shock, and even tilt. Moreover, the final buyer can access a complete record of information and trust that the information is accurate and complete.
Conclusion: what does the future hold for blockchain?
To conclude this guide on what the blockchain is, we would like to summarize our findings and what you’ve learned.
Initially, we showed the differences between DLTs, public blockchains and permissioned (or private) blockchains. To accomplish that, we’ve created an easy to read diagram, which details when each type of data structure should be used.
Afterward, we will dig deeper into what each type of system allows users to do. We compare the characteristics of a public blockchain with permission blockchains and distributed ledger technologies, or DLT. To help readers to understand these characteristics, we’ve used the example of the “blockchain trilemma”, which explains why it is not easy to scale a public blockchain and some methods used to accomplish that – besides using permissioned ledgers and DLT systems.
We discussed layer two technology, such as sidechains and childchains, payment channels, like the Lightning Network and Plasma, database sharding and even additional consensus algorithms.
Finally, we’ve presented the best applications of the blockchain technology, connected to the currency and payments industry, financial services and assets industry, such as funding, borrowing and lending, exchanges, ownership and oracles; and, finally, we’ve dug into the governance-side of the blockchain technology, like identity and open-governance products, and supply-chain tracking.
To conclude, we would like to exalt the importance of blockchain technology and why we believe it will change the world. In sum, by using public blockchain technology, agents are capable of disintermediating industries, making people more accountable for their actions and to increase transparency between players. Not only that but parallel technologies such as permissioned blockchains and DLT systems, allow for faster consensus between key industry players, which could substantially decrease production costs, legal costs, and information sharing costs.