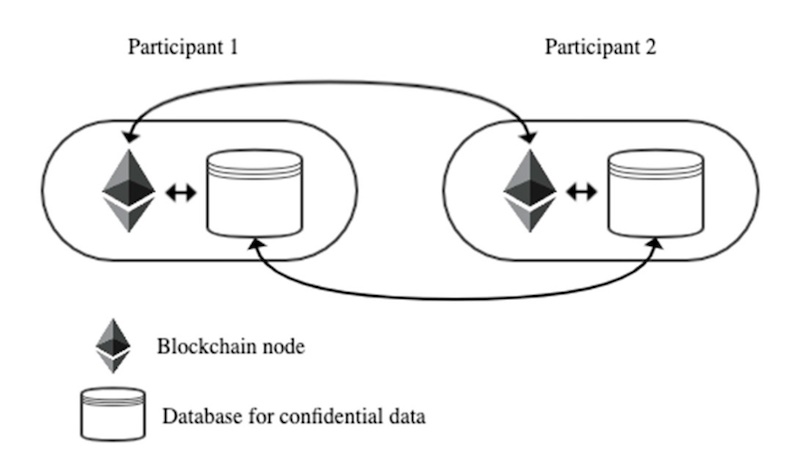
A zero-knowledge proof is a cryptographic technique that can help alleviate the security and privacy concerns at the forefront of traditional industries deciding whether to move their business operations to the blockchain. People think of the password as the standard protocol when solving computer security problems. However, the standalone password scheme can be too minute or random for many systems. Some protocols require better functionality to secure private transactions.
Therefore, research into zero-knowledge proofs began as a way to help authentication systems prove one party’s knowledge of a statement without revealing any additional information. This method embodies zero-knowledge, which is the primary focus of this article.
Moreover, zero-knowledge proofs can seem complex at first. So, if you need to start with something more basic, take the Crypto for Beginners course at Moralis Academy.
What is Zero-Knowledge Proof (ZKP) Technology?
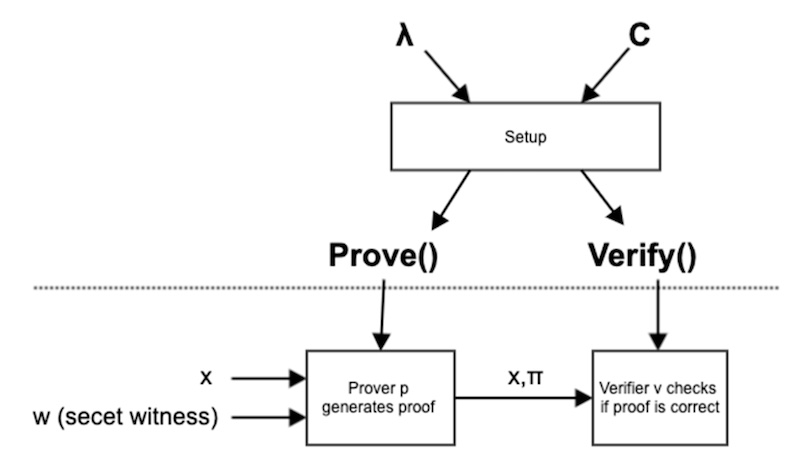
Zero-knowledge proof allows one user (the “Prover”) to prove they know a secret to another user at the other end (the “Verifier”) without revealing what the secret is. As such, “zero knowledge” means zero information about the secret gets disclosed. But the second party, the Verifier, can still validate that the Prover knows the secret.
This technology comes in handy when a user needs to prove they know a secret without revealing it. Such a situation would arise when a user doesn’t know or trust the other person with the information they possess. Nonetheless, they must still convince them that they know it. Thus, the benefit of using zero-knowledge proof is that it’s a way of authenticating communications without exchanging top-secret passwords. Communications remain secure and protected so no outside actors can eavesdrop and exploit the information a user is sharing.
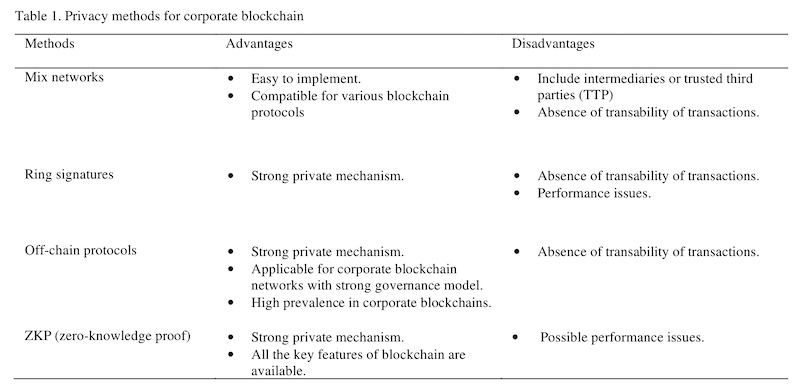
One use case for zero-knowledge proofs within cryptographic protocols is maintaining privacy while enforcing honest behavior. More importantly, for those involved in the cryptocurrency space, zero-knowledge proof methods fulfill the privacy requirements necessary to maintain the key features of blockchain.
Examples of ZKP Technology
Much of the information surrounding zero-knowledge proofs can appear quite technical. So, before we dig too deeply, let’s illustrate this methodology with some down-to-earth examples.
The Secret Cave Story
A well-known story called “How to Explain Zero-Knowledge Protocols to Your Children” presents the idea of zero-knowledge proofs. It uses two parties, “Peggy the Prover” and “Victor the Verifier”.
In the story, Peggy knows the secret word to open a magic door inside a cave. The cave is ring-shaped (see diagram). In addition, it has an entrance on one side with a magic door at the opposite end. Victor is trying to figure out if Peggy knows the secret word. However, Peggy doesn’t trust Victor (or anyone else) enough to reveal her knowledge of the secret word.
So, these two parties label the paths from the entrance “A” and “B.” Peggy enters the cave, but Victor must wait outside and is not allowed to see which direction Peggy takes. Next, Victor enters the cave and calls out which path (A or B) he wants Peggy to use on her return. If she doesn’t know the secret word to open the magic door, she’ll only be able to return down the path she started on. On the other hand, if she can open the magic door, it doesn’t matter from which direction Victor demands her return.
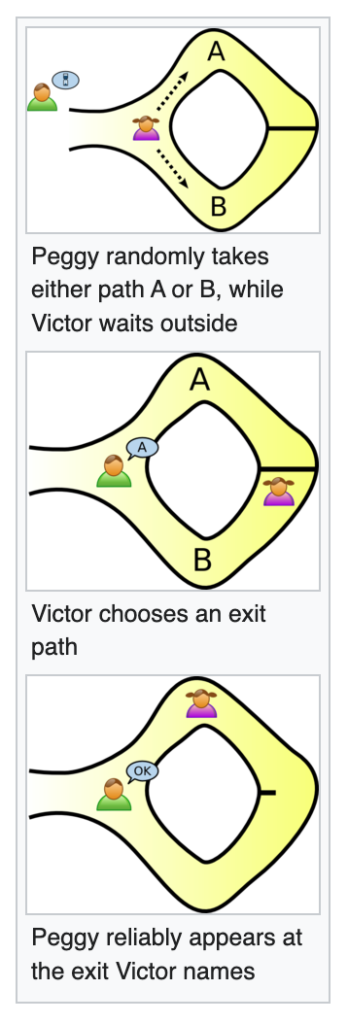
A 50-50 Chance?
Let’s suppose that Peggy does not know the secret word. In that case, she could only return by the path Victor named if she gets lucky, and his choice happens to be the same path she entered. Since Victor chooses A or B randomly, Peggy has a 50% chance of correctly guessing which direction Victor will call. However, the more the sequence repeats, the less chance she has of anticipating Victor’s requests. Eventually, the odds will whittle down to a one-in-a-million chance.
In other words, after enough call-outs resulting in Peggy successfully appearing at the proper exit, Victor can safely conclude that she does know the secret word to open the magic gate. More importantly, he knows she knows even though she never told him the secret word directly.
Further Proof
However, if Victor is still skeptical of Peggy’s success, she could further prove that she knows the secret word by having Victor accompany her to the mouth of the cave. There he could watch Peggy enter through A and exit through B. He could see that she knew the secret word to the magic door, and she was not making lucky guesses. Furthermore, she proved it without revealing the magic word to Victor. Below is another way to illustrate a zero-knowledge proof.
Why build on Solana? Solana is a layer-1 blockchain that competes with Ethereum, and Rust is its programming language. If you’d like to learn more about Rust & Solana, make sure to check out our blog at Moralis Academy!
The Colorblind Friend
Another example involves two friends. One is colorblind, and the other is not. There are also two identical balls of the same size involved. However, they are different colors. One ball is red, and the other is green. But to the colorblind friend, the balls are indistinguishable. So, the person who can see color wants to prove to his colorblind friend that the two balls are distinguishable. Furthermore, he wants to show that they have different colors without saying which specific colors they are. In other words, he does not want to reveal which ball is red and which is green.

Demonstrating a ZKP in Action
Here is how the zero-knowledge proof system works in this story. The colorblind friend puts the balls behind his back. Next, he reveals one ball and puts it behind his back again. When he shows it the second time, the other friend can tell him whether or not he switched the balls behind his back. He can tell based on the color. Furthermore, he can do this without telling his friend what color he saw.
Each time the colorblind friend asks, “did I switch the ball?”, the other friend will be able to answer correctly. Yes, there is a 50-50 chance he could guess correctly. But as the process gets repeated, the chances that he is merely guessing diminish. As he keeps making the correct call, the colorblind friend will become convinced that the balls are differently colored. This colorblind example demonstrates a zero-knowledge proof in action because the friend never learns which ball is red and which is green, yet he knows they are distinguishable.
As the bear market drags on, now is an excellent time to learn how to invest during a crypto bear market. Also, understanding crypto crashes will help you prepare for the next time it happens.
ZKP Properties
Now that you’ve seen a less technical demonstration of how a zero-knowledge proof works, let’s look at its properties. A properly functioning zero-knowledge proof of a statement must satisfy the following:
1. Completeness
Completeness is a method to verify if the statement is correct. If true, a Verifier (properly following the protocol) will become convinced by an honest Prover.
2. Soundness
If the statement is false, a Prover won’t succeed in convincing an honest Verifier that it is true. More specifically, the dishonest Prover, at best, has a negligible probability of succeeding. Because of soundness, the user must act honestly to provide valid proof.
3. Zero-Knowledge
When the statement is true, the Verifier learns nothing more than the fact that it is true. In other words, the Prover only needs to demonstrate they know the secret statement. They don’t need to reveal the secret. Knowing the information is sufficient. Because of “zero-knowledge”, the user does not compromise any privacy of the secrets it holds while providing proof.
The first two properties above are more general to interactive proof systems. The third property is what makes the proof zero-knowledge. Using a zero-knowledge proof forces a user to prove their behavior is correct according to the protocol.
More on ZKPs
Zero-knowledge proofs are not “proofs” in the traditional mathematical sense. That’s because there is a small probability (see “soundness” above) that a dishonest Prover can convince the Verifier of a false statement. Therefore, zero-knowledge proofs are probabilistic rather than deterministic proofs. However, techniques exist to decrease the soundness error to such tiny probabilities that they get relegated to the realm of negligible. Now let’s look at the different types. We can divide zero-knowledge proofs into two protocols: interactive and non-interactive.
Blockchain gaming and NFTs could be the catalysts that catapult us out of this bear market. Learn to build your own with our NFT coding tutorials.
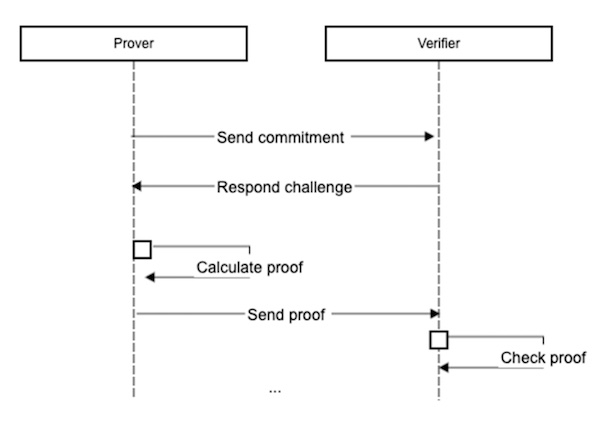
Interactive ZKPs
This type of ZKP requires interaction between the individual proving their knowledge and the individual who validates the proof. So, a protocol implementing zero-knowledge proofs must require the Verifier’s interactive input. Such input is typically in the form of one or more challenges to the extent that the Prover’s response will convince the Verifier only if the statement is true. The interactive process takes place when the Prover and Verifier are both online during messaging rounds applying the following steps:
1. The Prover sends a message to the Verifier called a “commitment”.
2. The Verifier replies with a string called a “challenge”.
3. The Prover sends a message using the commitment and the challenge.
4. Continue steps 1-3 until Verifier accepts the commitment.
The problem with such interaction is that it takes several rounds of communication. It reduces network performance and requires the Prover and Verifier to be online during the process. So, developers made protocol adjustments for the blockchain to accommodate non-interactive zero-knowledge proofs (NIZKs).
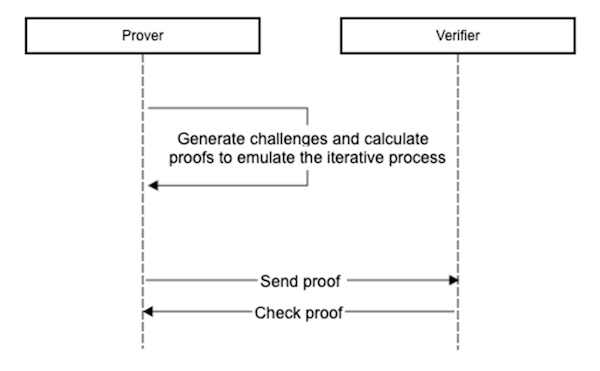
NIZK Proofs
The steps for NIZK protocols are a bit different:
1. The Prover generates a random number and calculates multiple challenges.
2. The Prover generates a proof (based on the challenges from step one) and sends it to the Verifier.
3. The Verifier ensures the proof is correct and responds to the Prover. Due to the lack of messaging rounds, NIZK protocols are more applicable to the blockchain ecosystem.
In addition, the NIZK scheme uses the following algorithms:
1. Setup
Setup is an initiation algorithm that sets security parameters.
2. Prove
This function generates proof by applying multiple challenges.
3. Verify
The Verify function receives an input parameter and outputs a boolean value.
As you can see, verifying that the Prover possesses the knowledge claimed takes work.
ZKPs and the Blockchain
As far as the blockchain goes, the Zerocoin and Zerocash protocols first applied zero-knowledge proofs, ultimately leading to the birth of Zcoin (now Firo). Zerocoin has a built-in mixing model to ensure anonymity. Furthermore, users can transact in a base currency and then cycle it in and out of Zerocoins. Zerocash uses a NIZK proof. The difference between the two is that Zerocash can conceal the transaction amount while Zerocoin cannot. In 2018, developers introduced “bulletproofs” as an improvement to NIZK proofs since no trusted setup is needed. The popular privacy coin, Monero, later implemented bulletproofs into its protocol.
Celsius is another casualty of this bear market. Find out what’s happening with Celsius Network in our recent blog article.
Zero-Knowledge Proof Technology – Summary
As blockchain is getting adopted within various industries, the sector must tackle challenges in order to take off. As such, zero-knowledge proof technology might be the answer. To sum up, the essence of zero-knowledge proofs is that “revealing secret information to prove that one possesses knowledge of it is trivial”. The challenge, then, is to prove one has confidential data without showing it.
If you want to see examples of zero-knowledge proofs in today’s cryptocurrency market, check out zk-STARKs and zk-SNARKs. They are two of the most promising ZKP technologies on the market.
If you’re ready to take your blockchain skills to the next level, enroll at Moralis Academy and learn how to become a blockchain developer today!