The bZx Protocol is a Ethereum-based DeFi lending protocol which users can borrow, lend, and margin trade without relying on third parties. In the past, margin traders had to use centralized exchanges (CEXs). And while decentralized exchanges (DEXs) can have vulnerabilities, CEXs have many weak points that can be exploited.
These potential CEX weak points include such things as hacks, looming regulation, insider impropriety, and just plain mismanagement of funds by people in positions of trust. As such, the bZx Protocol, among other things, seeks to offer margin trading in a truly decentralized fashion.
The bZx Protocol is just one of countless DeFi applications out there. If you want to learn more about the world of decentralized finance, cryptocurrencies or blockchain technology use cases in general, you should check out Ivan on Tech Academy! Ivan on Tech Academy is one of the largest online blockchain education platforms, and offers a wealth of crypto courses and in-depth educational information. Start taking part in the blockchain revolution today!
The History of bZx
Tom Bean and Kyle Kistner are the co-founders of bZx. They came up with the idea in 2017 and released the white paper in February 2018. By December of the same year, they had raised close to $8 million in an ICO. In June 2019, they launched Fulcrum, the trading front end. And in October 2019, they launched Torque, the lending front end.

Why Use bZx?
Like other DeFi platforms built on Ethereum, bZx’s smart contracts automate the financial process. Now, bZx is similar to dYdX. However, the team’s goal is to make sure that “everything is tokenized.”
The biggest difference between bZx and others in their field is the three tokens it uses: iTokens, pTokens, and the BZRX token. Each of these tokens plays a vital role in how bZx operates.
bZx also distinguishes itself in how it incentivizes yield farming by awarding active users with half of the fees payable through their BZRX token.

And the team dedicates itself to decentralization. This is evident in their use of decentralized price feeds for calculating interest as well as how they work to keep gas fees low despite the growing number of supported assets on the platform.
bZx Tokenomics
BZRX is bZx’s governance token that allows its holders to vote as well as to stake their tokens to earn a share of the protocol fees.

Borrowers and lenders on bZx move funds in and out of global liquidity pools that different exchanges share. The bZx platform uses iTokens and pTokens for this.
So, when lenders supply funds to liquidity pools they receive iTokens. These are prefaced with an “i” and represent the lender’s claim on their supplied funds. iTokens can also earn compound interest. And the good news is that these tokens can be redeemed for the original funds plus interest at any time.
But, when users borrow funds to open trading positions on margin, they receive pTokens. The “p” stands for position and it can represent either the long or short side of a margin trading position. Moreover, users can also get iTokens and pTokens on certain DEXs like Uniswap and Kyber. Typically, however, these tokens are just created directly by using bZX.

How To Use bZx?
You can enter the bZx platform through either front-end: Fulcrum or Torque. In the spirit of DeFi, no registration is necessary, and bZx doesn’t take custody of your funds. You just need to connect with MetaMask or some other Ethereum wallet.
For margin trading, you’ll want to use Fulcrum, bZX’s trading front end. On the other hand, you’ll want Torque for bZx’s lending front-end. This is where you can borrow funds at a fixed interest rate which helps keep loans more predictable. Also, Fulcrum limits borrowing to “trades only” whilst Torque allows borrowers to use the money for whatever they want.
The bZx Hacks
Now for the bad news. bZx has received a lot of attention this past year but not always for the best reasons. Hacks have plagued the fledgling protocol not once, not twice, but three times to the tune of an estimated $1 million in damages.

It’s usually nice to be the first, but not in this case. bZx holds the honor of being the first DeFi platform of substance to get hit with a large attack. It also holds the distinguished honor of being the second DeFi platform to be attacked. Two back-to-back hacks brought the project to its knees and forced the team to retreat to the sidelines to reconfigure the protocol whilst everyone else was profiting handsomely during this year’s peak of the DeFi boom.
Looking to learn more about the various DeFi projects that shot to prominence during the DeFi boom? Ivan on Tech Academy offers in-depth looks at most of the high-profile DeFi protocols and projects. What’s more, if you enroll in the various blockchain courses on Ivan on Tech Academy using the promo code BLOG20, you can get a whopping 20% off!
bZx Hack #1
The problems started back in February of this year while the founders were traveling to the ETHDenver conference. At an afterparty, they noticed the interest rates for ETH were climbing abnormally. Next, they found a suspicious transaction that earned the user approximately $300k. What happened was a hacker took out a flash loan for 10,000 ETH and borrowed 112 wrapped Bitcoin (WBTC) from Compound. He then opened a 5x short position against ETH-BTC on Fulcrum.

Next, the hacker swapped 51 WBTC on Uniswap. With these trades, the attacker caused enough slippage in the market to exit his short position, pay back the initial flash loan, and keep the rest for himself.
Problems at ETHDenver
So, while everyone else partied at ETHDenver, the team had to jump into action. It wasn’t like they could just press a giant “Pause” button. Fortunately, however, they were able to freeze the entire system by cobbling together a hack of their own that included disabling the oracle whitelist.
Thankfully, this stopped the bleeding. However, it was an embarrassing situation to have to endure in the presence of their DeFi peers.
Luckily the protocol did not automatically spread the loss of $300k to all of bZx’s users. Users got their money back and the team promised multiple upgrades. These included using the administrator key to prevent further attacks of this sort. They also delisted the ETH-BTC margin tokens as well as implemented maximum trade sizes.
When all was said and done, the others at ETHDenver were supportive and even congratulatory of how the bZx team handled their business. At least, that is, until the second hack.
bZx Hack #2
Hack number two happened soon after the system update. This time the attacker took advantage of bZx’s flash loans and walked away with a cool 2,388 ETH.
Once again the team was on a retreat in Colorado when an unusual transaction caught their attention, involving a flash loan.

It didn’t take long to figure out something was wrong. Unfortunately, the team had to pay their restaurant bill without eating. Supposedly leaving hundreds of dollars' worth of uneaten food on the table, they bolted out into the Colorado snow to man the battle stations.
This hack went down as follows: The attacker took out a flash loan of 7,500 ETH and bought sUSD which was trading close to the $1 mark. He then deposited the sUSD on bZx as collateral. Next, the attacker used 900 ETH to buy more sUSD on both Kyber and Uniswap. This action pushed the price over the $2 mark.
A Hacker Claims His Prize
After the price of sUSD shot up, the hacker borrowed approximately 6,800 ETH against sUSD on bZx to repay his flash loan. When it was all said and done, the attacker earned close to $645,000.
The team quickly paused the system and began diagnosing the issue. Fortunately, they knew how to handle it. Unfortunately, the same people who sympathized with their plight in the first hack weren’t as forgiving the second time around. Especially since the second hack occurred within such a short span. It would only be natural for the team to get paranoid that the term “incompetence” might spring to mind.
Diagnosing Both bZx Hacks
It turns out that the first hack was more of a typo-level bug that resulted from not having proper processes in place. The team wrote this off to not having big venture capital money behind them like other DeFi protocols.
In the second hack, the main vulnerability turned out to be their reliance on Kyber as an oracle. The team recognized that Kyber wasn’t an optimal solution, but they felt the auditors should have also flagged it. Chainlink wasn’t an option at the time, however, so they centralized their oracle.
So, although the team blamed the second exploit on oracle manipulation, these attacks nonetheless set off a discussion in the DeFi community regarding the danger of flash loans.
Two Hacks Are Not Better Than One
The two hacks forced the team to shut bZx down, reflect on what went wrong, and start rebuilding. It would have been easy to write it off to bad luck, or a superstitious bias towards Colorado retreats. However, what it boiled down to was the team having to admit to their shortcomings as well as a bit of blame-shifting onto their security auditors.
Auditing Smart Contracts
Smart contract auditing is a crucial step to any protocol’s prelaunch. That’s because everyone considers unaudited platforms to be high risk.
In an interview, the team admitted they were still “green” when they put the first version of bZx onto the testnet. Nor did they know any security auditors or much about the process of auditing smart contracts itself.
One thing they learned quickly though is that not all auditors are equal. Eventually, they chose ZK Labs to conduct the audit. However, they were not happy with the $50k price tag nor the service.
bZx Hack #3
If you’ve read this far, you’re probably wishing the bad news would end. But bad things seem to happen in threes. And shortly after September’s relaunch, hackers targeted bZx yet again!
The third hack amounted to approximately $8 million and was blamed on a smart contract loophole. The lead engineer at Bitcoin.com had already discovered this loophole (defined as a “duplication vulnerability”) and reported to bZx that millions of dollars were at risk.
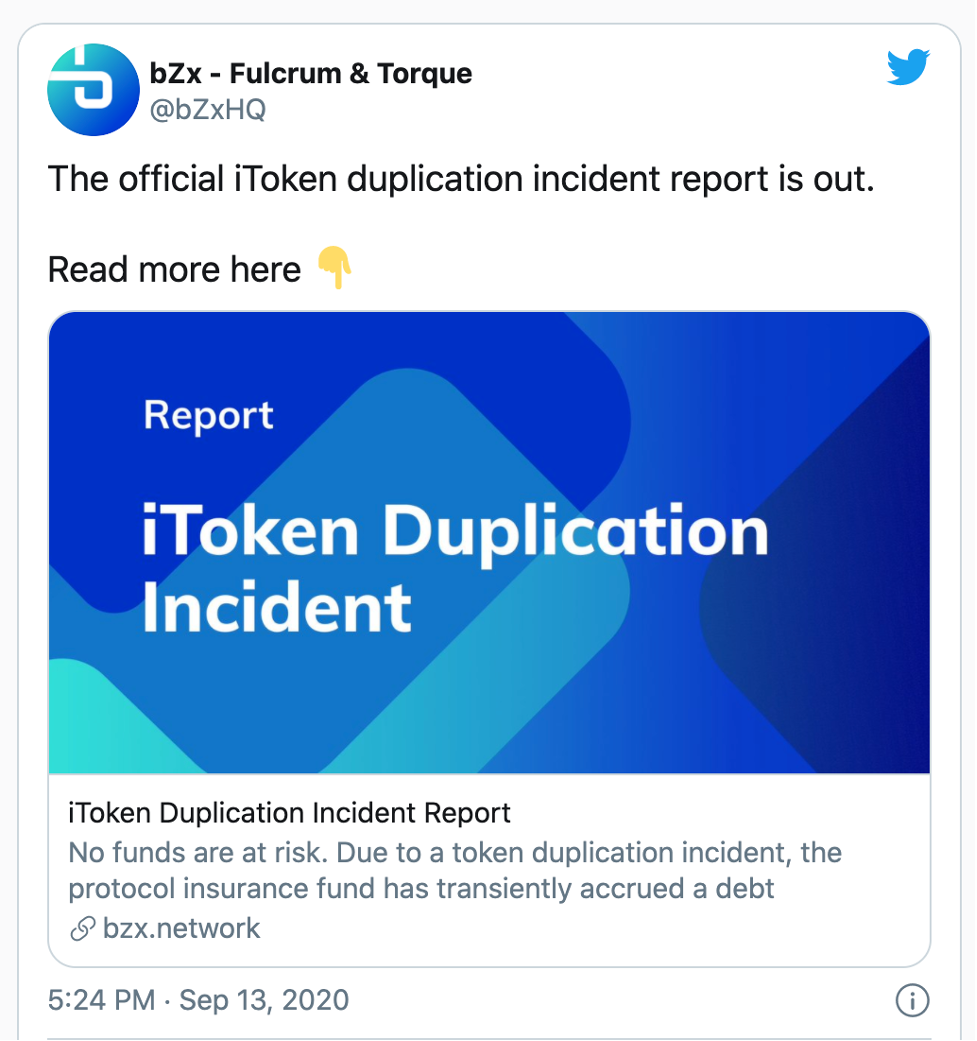
Well, a hacker found this same loophole which allowed him to mint 219,200 LINK tokens, 4,503 ETH, 1,756,351 USDT, 1,412,048 USDC, and 667,989 DAI in total.
The team first noticed the attack which caused unusual movements in the protocol’s total value locked (TVL). They then identified strange goings-on with the transferFrom() function on the iToken contract.
The transferFrom() Function
Now, the hacker knew that ERC-20 tokens have a transferFrom() function. This function is responsible for transferring tokens. And in this hack, the attacker figured out how to call this function to create and transfer iTokens to themselves. By doing so, they artificially increased their balance.
When the team caught wind of the breach, they immediately halted the minting and burning of iTokens. And they sent a patched version of the source code to their security auditing firms, Certik and Peckshield. After the review was complete, the team deployed the new version of the iToken smart contract.
Co-founder Kyle Kistner calmed investors’ fears by reassuring them that none of their funds were at risk. And the hacker ended up returning the money after he was tracked through on-chain analytics.
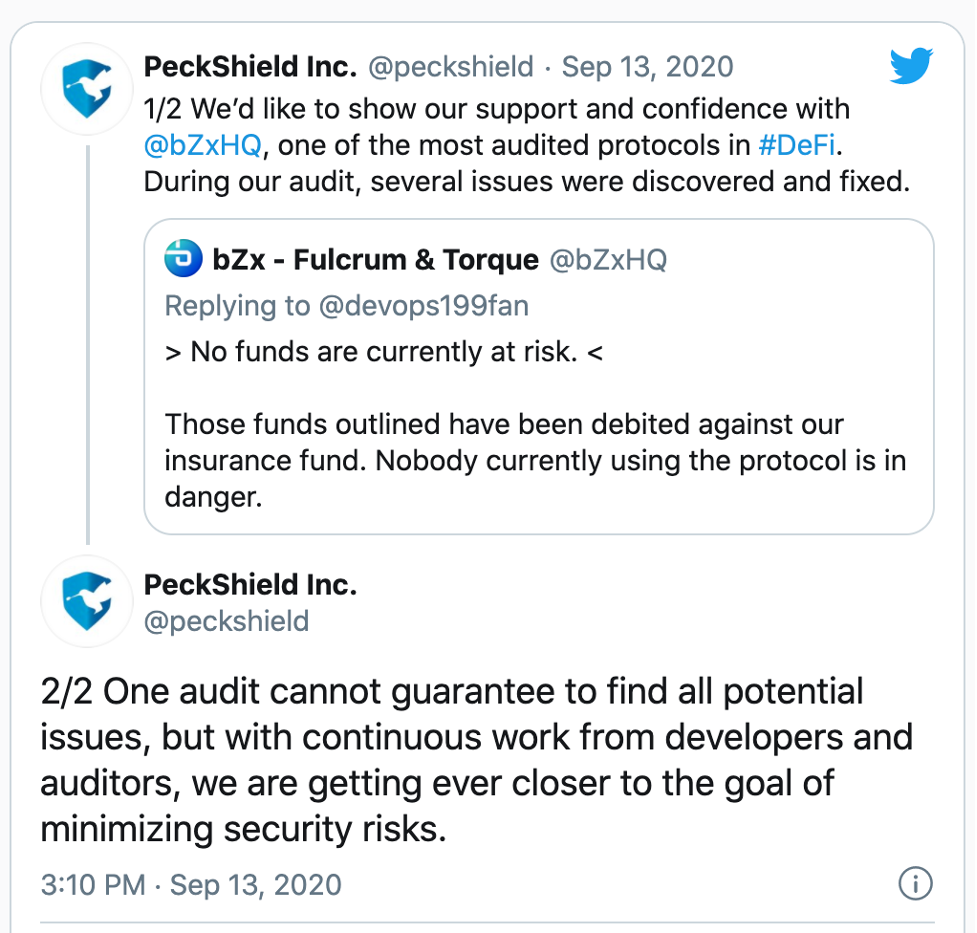
When it was all said and done, they blamed defective code for the attack. It allowed the hacker to duplicate the assets and increase the balance of iTokens. The team also blamed their auditing firms, PeckShield and Certik for failing to catch the flawed code. This in turn incited the PeckShield firm to respond with: “One audit cannot guarantee to find all potential issues…”
The Future for bZX
Thankfully none of the customers lost their funds during the attack. And while three hacks might have crippled the spirits of an ordinary founder, Kistner remains optimistic about bZx’s future. Three hacks is a lot to take and this crazy year of 2020 isn’t over yet, so fingers crossed.

Kyle Kistner, bZx co-founder
However, with the rapid growth of DeFi, we can assume that some of the startups launched with buggy code in their zeal to ship. Hopefully, bZx’s problems are behind them, and fortunately for them, their trading volume is still growing.
After all, their zeal for decentralization is commendable. And with all the complex systems that developers can build on top of each other in DeFi, bZx has a lot to offer.
By combining such things as TokenSets with bZx’s iTokens, creators can build completely new products. Other dApps like DeFiZap have created products that use bZx’s pTokens to leverage new trading strategies. And we must all remember that DeFi is still in its infancy so there are much bigger things on the horizon.
Do you want to learn how to code Ethereum smart contracts? How about learning how to become a smart contract security auditor? If so, visit Ivan on Tech Academy to kickstart your world-class blockchain education!
Author: MindFrac