With ETH 2.0 just around the corner, now is a good time as any to look into one of the most critical updates it’s bringing along – proof-of-stake (PoS). In this article, we will look at why the current proof-of-work (PoW) system isn’t refined enough for future scalability needs and then see how eth 2.0 is looking to integrate PoS.
What is Proof-of-Work?
Quite like Bitcoin, Ethereum also uses a proof-of-work (PoW) consensus protocol. The core principle of PoW works like this:
- Specialized nodes in the network called “miners” own mining equipment called “ASICs.”
- The miner takes up transactions from the mempool to form a block and then hashes its contents.
- They then add a random value called “nonce” in the front of the hash and then hash the overall value again.
- Now the miner will compare the value of the hash against the network difficulty. The difficulty is a metric decided upon by the network, which adjusts according to the ease with which the miners are mining blocks in the network.
- The total hash value has to be less than the difficulty. If it isn’t, then the whole process is repeated until it is.

Disadvantages of PoW
Ethereum is planning to move on from PoW due to its several issues:
- PoW consumes a lot of unneeded resources. Miners eat up a lot of power in their attempt to solve complex equations. This makes the whole process highly inefficient and non-desirable.
- Wealthy organizations can afford to buy expensive ASICs, giving them an unfair advantage over the competition.
- Because of this centralization of wealth and resources, these organizations often tend to have the lion’s share of the network hashrate and tend to produce the blocks more frequently.
- As of writing, the top 3 mining pools own more than 50% of the network hashrate. Theoretically speaking, these thee can join forces and launch a 51% attack on the network.
- Bitcoin consumed more power than the entire country of Switzerland in 2019.
- PoW can’t provide instant finality. Since it takes time to mine a block (around 25 seconds in Ethereum). As such, a transaction done in a PoW system is, by no means, final.
What is Ethereum Proof-of-Stake?
Proof of Stake (PoS) has already become one of the most sought after consensus protocols in the space. The idea is simple. Lock up a part of your tokens in the system and become a validator in the network. Following that, this is how the process will work:
- The validators will begin to validate the blocks by signing off on them.
- When the block gets approved, they receive a reward that’s proportional to their stake.
- Once a validator agrees to stake its tokens, the stake is locked up.
- The amount of times that you get to validate a block is directly proportional to your stake. Someone staking 1% of the total overall value will get to validate 1% of all blocks.
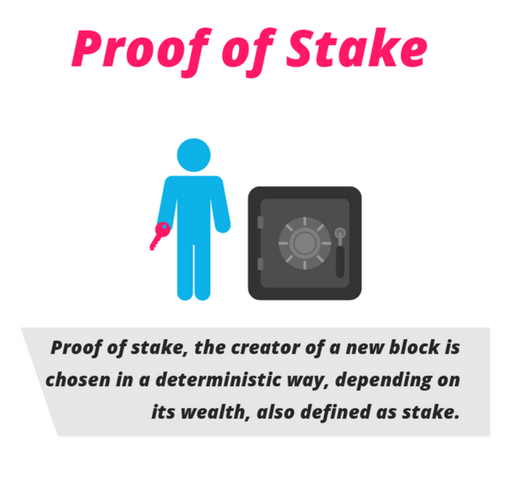
Proof-of-Stakes biggest weakness – Nothing at stake
The biggest problem with PoS is the “nothing-at-stake” problem. To understand what we mean by that, consider, the following issue:
So consider the situation we have above. There is a main dominant chain (blue) and a secondary chain (pink) that’s branching out of it. Typically, an honest miner/validator should append blocks to the longest chain. However, what if a malicious miner Alice chooses to mine on the red block and overwrite the transaction history written in block B, C, and D?
In PoW, the sheer costs involved can quickly mitigate this situation. Since the miner has to spend so much of their resources just to mine one block, they have no incentive to go against the rest of the system. After all, they don’t want to do all that work for nothing, right?
However, PoS is a different story.
In PoS, a validator can simply place a bet on both the blue and pink chains. Whatever chain gets a successful addition, the block reward should be enough to compensate them for their losses. In this case, we are looking at a situation where no matter what the attacker does, they will still be in an advantageous position.
This is the biggest issue with PoS, the “Nothing at Stake” problem. To make sure that the attacker doesn’t freely move around the chains, Ethereum will use the Casper Protocol.
Casper Protocol – Eth 2.0 Consensus Mechanism
Casper changes the PoS game by bringing in a punishment factor to keep all the validators honest. To understand how this works, let’s look at the standard PoS system and observe how Casper changes things.

- Validators can stake a portion of their stake in the Ethereum network.
- They then validate the blocks they believe will become a part of the main blockchain.
- If they validate the wrong block, their stake will be completely slashed off.
- However, if they act in the interest of the system, they will get the appropriate block reward.
As you can see, Casper acts in the interest of the entire network by aligning individual goals with the goals of the whole network. Since malicious validators have a lot to lose (i.e., their stake) they are forced to act honestly. Along with this, validators will also have to be very careful about their node availability. If they are not available in time to validate their blocks, they will risk losing their stake altogether.
Casper the Friendly Finality Gadget vs Casper Correction-by-Construction
Casper actually consists of two different algorithms. The first one is called “Casper the Friendly Finality Gadget” or Casper FFG and the other is “Casper Correct-by-Construction” (Casper CBC). So, let’s put each of these under the limelight and see what they are about.
Casper FFG
Casper FFG has been worked upon by Ethereum founder Vitalik Buterin himself. FFG will be a hybrid PoW/PoS consensus mechanism that’s going to make the transition from PoW to PoS extremely smooth. The idea behind it is pretty simple:
- The underlying consensus will continue to be the traditional PoW.
- Every 50th block is going to be a checkpoint finalized for the PoS chain. Once a block has crossed the checkpoint, there will be no going back.
The way it achieves this is by layering the PoS protocol on top of the ethash PoW protocol.
What does Finality mean?
Finality is a quality wherein an operation, once executed, gets forever etched in history. Nothing that you can do will ever erase or reverse it. When it comes to monetary matters, finality is an absolute must. Eg all your mutual funds must have full finality. Imagine if tomorrow, because of a software error, you lose all your funds? Mutual funds investment, as with all monetary interactions, must have complete finality. According to some, PoW is the only way to achieve 100% finality. However, as we know, the process is hugely wasteful.
Casper FFG claims that it can provide complete finality, provided 2/3rd of all the validators make bets on the finalized blocks. As with any byzantine fault-tolerant system, Casper assumes that less than 2/3rd nodes in a network will be malicious. To illustrate how Casper FFG will help ETH 2.0 achieve stronger finality, let’s see an example:
- Imagine there is a network with three nodes A, B, and C.
- B is a malicious node.
- A and B sign off one claim, while B and C sign off on the other one.
- As you can see, no matter what happens, either A or C, i.e., the two honest stand to lose quite a lot if the other’s claim comes true.
- This is why the validators have no reason to collude and act maliciously.
- If we do have a double finality situation in the rarest of cases, then the claim that gets the maximum votes automatically becomes the dominant chain.
This feature of FFG is known as Total Economic Finality. As Vlad Zamfir puts it, “Imagine a version of the proof of work where if you participate in a 51% attack, your mining hardware burns down.” In other words, there is little to none economic incentive for validators to go against the system.
Fork Prevention in FFG
Casper FFG also has mechanisms for fork prevention. Instead of blindly choosing the longest chain, FFG follows and tracks the justified checkpoint of the greatest height. To understand what we mean by that, check out the following diagram.
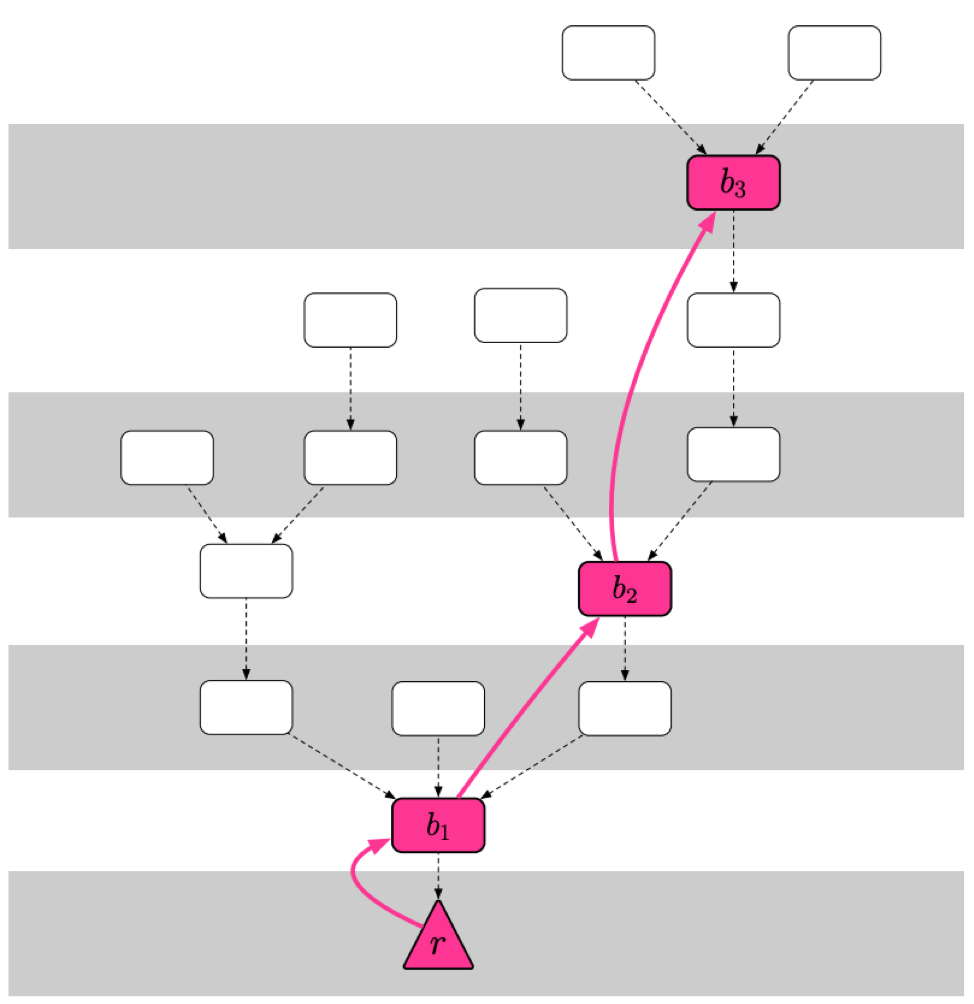
As evident from the diagram, the correct chain is r->b1->b2->b3.
Casper CBC
To understand how a correct-by-construction protocol differs from standard protocol design, let’s first examine how the latter works.
- You first specify a protocol and define the properties that it must satisfy.
- Prove how the protocol completely satisfies the properties.
As you can see, this is a pretty statically-defined protocol. Now, let’s look at how a CBC protocol works:
- The developers put in some of the initial work and partially specifies the protocol.
- The developer then specifies the properties.
- The protocol then derives itself according to the properties.
So, if you think about it, CBC allows the protocol to derive itself dynamically, and one of the ways it does so is by declaring an “ideal adversary.” An ideal adversary is a metric that:
- Lists all the failures that can happen to the protocol.
- Continuously fine-tune the protocol until it’s complete.
ETH 2.0: LMD Ghost protocol
The LMD Ghost fork choice allows you to choose the most optimal chain instead of the longest one. To understand how it works, take a look at the following diagram:
- Casper inspects the tree of blocks from the genesis block and goes up in the tree’s hierarchy.
- At every step, the protocol takes a decision depending on how much support a particular block has.
- The diagram above shows five validators – A,B,C,D, and E. Each of these has created a block during different time periods.
- In the diagram, we have two paths for the blockchain to take -> A-B-D or A-B-C-E.
- The support commanded by the last block determines the correct path. We learn the course of this path by looking at the hierarchical positions of the blocks.

The Staking Process
As you can see, we have divided the entire state into 7 positions.
- Position 1: The block here has been created by A. It has been validated by ABCDE, so the node weight is 5.
- Position 2: The block here was created by B and has been validated by everyone. Hence the weight is 5.
- Position 3: This is where things get interesting. We have a fork since there are two blocks created by C and D. Block D has been validated by only D so its weight is 1. Block C has a weight of 4 as it has been validated by ABCE.
Hence we can deduce that the correct path here is A,B,C,E.
Another interesting part about this protocol is that a minority of the network can never beat a majority. Once again, consider the image above, let’s bring it back here:
If the validator D continues to validate blocks on the A-B-D path at a rate that’s faster than the one in the other chain, it will still be rendered useless, since Ethereum 2.0 will only consider block weight as a valid metric.
ETH 2.0 – Casper Protocol Features
- A node must stake at least 32 ETH to participate in the consensus mechanism.
- In a PoS system, you can participate with a simple laptop or computer.
- Every time a block is potentially proposed, the protocol automatically chooses anywhere between 4 and 64 random committees of 128 valid nodes.
- This makes the protocol provably secure as it ensures that there is a less than a trillion chance of the 1/3rd malicious validators to take over the network.
- The rate of return for Casper has been calculated to be anywhere between 4%-10%.
When is Ethereum Casper Protocol Launching?
The first iteration of Casper will be launched in 2020 with the Phase 0 of Ethereum 2.0. The first instance of this transition will be in the form of the beacon chain, which will manage the registration of the validators. The first block of the beacon will launch only upon meeting the following conditions:
- At least 524,288 ETH.
- The network has at least 16,384 validators.
During this phase, Ethereum will continue to be mainly a PoW chain, while the beacon runs in the background. Later on, in Phase 1.5, the beacon and PoW chain will join together to create the Ethereum 2.0 PoS chain.
How does Casper address the shortcomings of PoW?
Casper will help in addressing the three biggest problems with PoW:
- Accessibility.
- Centralization.
- Scalability.
Accessibility with Staking Pools
The barriers to entry for a PoW blockchain is exceptionally high. Miners have to consider a lot of factors, such as:
- Initial hardware costs.
- Power and electricity.
- Regular maintenance and updates.
When it comes to staking, any average user will obviously get intimidated by the initial minimum investment of 32 ETH (~$6,500). However, Ethereum allows their validators to run “staking pools.” Similar to how mining pools work, validators will be able to pool in their ETH tokens and receive rewards that’s proportional to the percentage of their stake within the pool.
Decentralizing the Power
The centralization issue with PoW is definitely a huge problem. As mentioned before, Bitcoin’s hashrate distribution is extremely centralized, with three mining pools owning over 51% of the network hashrate. The reason why this is dangerous is because of something called 51% attack.
In a 51% attack, a malicious entity gains full dominance over a decentralized network by owning more than 51% of the overall hashrate. In this situation, they have the power to:
- Hardfork from the protocol whenever they see fit.
- Mine a vast majority of the blocks in the network.
As you can imagine, this can be extremely catastrophic to the network. So, how does Ethereum do when it comes to hashrate distribution?
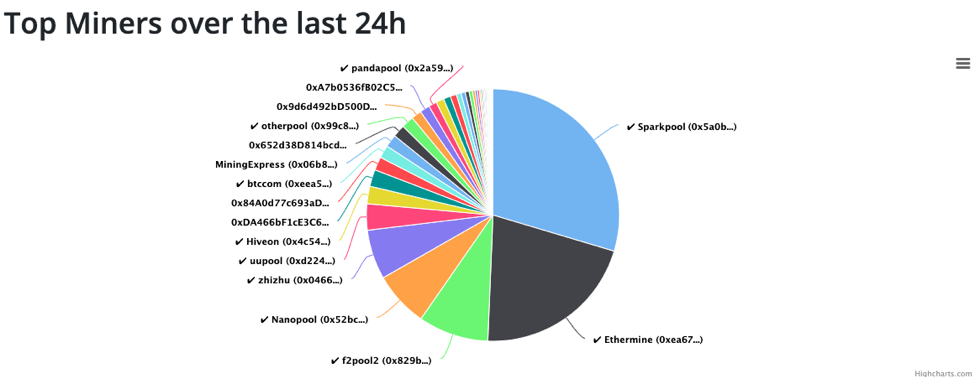
Oh dear….
Apparently, over the last 24 hours, two pools – Sparkpool and Ethermine – managed to hoard over 50% of the network hashrate. This is really not a good look now, is it?
However, with PoS, there will be significantly fewer barriers to entry and removes any sort of hashrate centralization. You will only need three things to be a validator in a PoS chain:
- Some crypto.
- A computer/mobile phone.
- An internet connection.
Scaling up with Sharding
The two most critical upgrades in Ethereum 2.0 are the implementation of PoS and Sharding. While it is possible to implement Sharding with PoW, it will be extremely difficult to execute it properly.
The two most critical upgrades in Ethereum 2.0 are the implementation of PoS and Sharding. While it is possible to implement Sharding with PoW, it will be challenging to execute it properly.

To understand why, think of a pizza. Now think of a single slice taken out of that pizza. Which one will be easier for you to eat? The slice, right?
The same concept holds for a blockchain and its shards. Shards are fragmented states of the blockchain i.e., slices of the pizza. The individual shards’ hashrate won’t be anywhere close to the main chain’s hashrate. This is why a miner with a considerable amount of hashrate will be able to take over the shard easily.
On the other hand, in PoS chains, it is possible to know who the validators are due to the address attached to their deposit. Through a provably randomizing algorithm, these chains can make sure that the validators selected to validate a block in the different shard chains are entirely random.
Conclusion: ETH 2.0 Casper Protocol
Ethereum 2.0 is going to be truly monumental. While Casper integration is definitely the biggest change, there are other amazing innovations as well, such as – Sharding, raiden, plasma, eWASM, etc. We will be looking into each one of these innovations in the subsequent articles, starting with Sharding.
If you are interested in learning more about the ins and outs of Ethereum before ETH 2.0 kicks in, check out some of the courses available on one the world’s most successful blockchain education platforms, Ivan on Tech Academy. We have several high-value accredited courses on blockchain and cryptocurrency that have been created by our in-house trainers and industry experts. Along with Ethereum, the run-up to ETH 2.0 and the different phases of ETH 2.0, we also cover blockchain basics and have several developer courses, as well.