It’s no secret that the Decentralized Finance (DeFi) field has exploded in 2020. The year started with DeFi, claiming approximately $700 million in total value locked (TVL). However, that number has rapidly ballooned to $16 billion, according to DeFi Pulse. Unfortunately, new investors weren’t the only ones attracted by the big numbers. A fair share of hackers has climbed aboard to profit as well.
With the DeFi industry still in its infancy and founders in a hurry to launch, it’s no surprise that they made some mistakes. However, some of the hacked protocols had gone through proper smart contract security audits and still got hacked. Alas, such are the risks associated with a nascent industry.
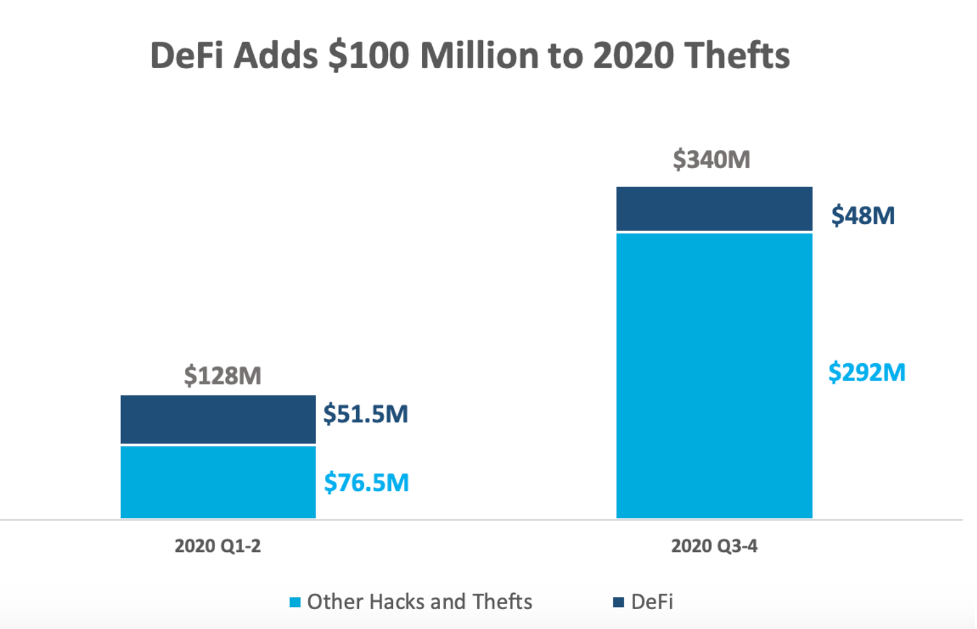
DeFi protocols are hardening and becoming more resilient, but 2020 was still a profitable year for hackers. In the first half of the year alone, DeFi hacks amassed over $51 million. Meanwhile, with half of December gone, that number has practically doubled to over $100 million.
Let’s look at some of the year’s significant DeFi hacks, the protocols involved, and the exploits used (we’ve rounded the numbers for simplicity). If you want to know more about the DeFi field and how to make sure you minimize the risk of suffering a hack, you should check out Ivan on Tech Academy to educate yourself regarding crypto. Ivan on Tech Academy is one of the leading cryptocurrency education platforms, and over 30,000 students have already enrolled.
DeFi Hacks – 2020 Timeline
- bZx – February 18 ($1 million)
- dForce, April 19 ($25 million)
- Harvest Finance, October 26 ($34 million)
- Cheese Bank, November 6 ($7 million)
- Akropolis, November 12 ($2 million)
- Value DeFi, November 14 ($7 million)
- Origin Protocol, November 17 ($7 million)
- Pickle Finance, November 21 ($20 million)
- Warp Finance, December 17 ($8 million)
Three Types of DeFi Hacks
To be sure, there are more than three ways to crack a smart contract. However, these three were prominent in 2020.
- Reentrancy Attack
This attack can happen if a contract makes an external call to another untrusted contract before resolving. For example, if it transfers funds before setting its balance to zero, an attacker can beat the withdraw function to death and essentially drain the entire contract.
However, not every call can be an internal one, so devs must be careful to ensure the external calls are safe. Otherwise, an attacker can re-enter the contract and do bad things. Akropolis, dForce, and Origin were all hit with Reentrancy Attacks.
- Price Oracle Manipulation
This kind of DeFi hack is becoming more popular because smart contracts need to get token price information. You might have heard of Chainlink, but decentralized exchanges (DEXs) are also oracles. It’s easy to query the spot price of a token on a DEX like Uniswap. The problem is, attackers can temporarily manipulate these prices to carry out their exploits.
bZx, Cheese Bank, Harvest, and Valley were all hit with price oracle manipulation exploits.
- Logic Errors
These kinds of errors can be hard to categorize because they are unique to the contracts where they reside. For instance, it was a logic error that opened up Pickle Finance to an exploit.
BZX Hack #2, February 18, 2020
Poor bZx had a tough 2020 getting hacked three times. You can read about those in our bZx protocol article. Here, we’ll only examine Hack #2.

This hack came right after the first one, forcing bZX to pause their protocol again. Like the first time, the attacker used an undercollateralized loan. However, this time they switched up the DEX and the collateral.
The attacker used ETH to purchase almost all of the sUSD tokens available on Kyber. He/she then purchased more sUSD from Synthetix and deposited it with bZx. With all this sUSD as collateral, the attacker could then borrow the maximum amount of ETH.

The Steps:
- Borrow 7,500 ETH from bZx.
- Swap ETH for sUSD on Kyber to drive up the sUSD/ETH market price.
- The spiked sUSD/ETH allows the attacker to borrow more ETH.
- This loan is now under-collateralized.
5: Repay the Flashloan to bZx.
With the borrowed ETH, the attacker could repay bZx their 7,500 ETH flash loan and still profit 2,378 ETH.
dForce Hack – April 19, 2020
dForce is a Chinese-based startup with big dreams. Their goal is to set up a wide range of financial operations and become a DeFi super network. The team had just secured investments by some big players such as CMBI, one of China’s largest bank subsidiaries, before getting chopped for $25 million in April’s DeFi hack.
It happened when LendF.me (their lending app) got hit with a reentrancy attack. The hacker has since converted the stolen funds on various DEXs.
Harvest Finance Hack, October 26, 2020
DeFi hacks quieted down somewhat over the summer, but the hackers returned with a vengeance in the Fall. Harvest Finance suffered seven minutes of hell as an attacker seized the assets inside Curve’s yPool. And in those short minutes, Harvest got a harvesting of its own for a whopping $34 million.
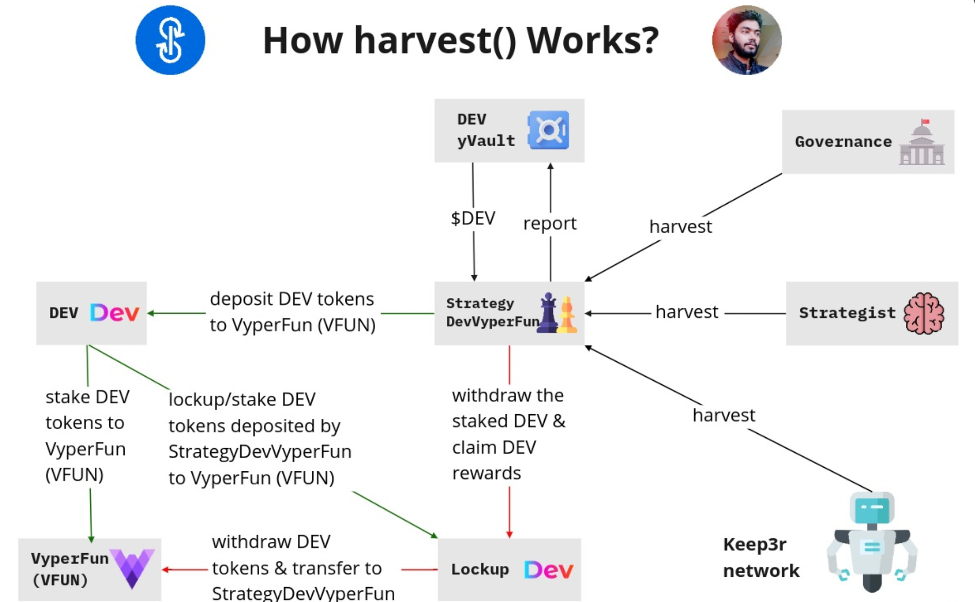
This hacker once again fed off of flash loan superpowers. And armed with an understanding of arbitrage, impermanent loss, and slippage, successfully tanked the USDC and USDT vaults.
With the price of USDC and USDT at artificial lows, the attacker could purchase them way below market value. In the end, he repaid the flash loan, took the excess as profits, and also received a $100k bounty on his head courtesy of the Harvest team.
Cheese Bank Hack, November 6, 2020
Cheese Bank wants investors to have the option to manage their assets their way. However, they had a flawed approach to measuring collateral with price oracles, which cost them over $3 million in November’s first DeFi hack.
Rats are attracted to cheese, and at least one intelligent rat figured out how to manipulate the collateral price on Uniswap with a flash loan from dYdX. As we’ve seen, flash loan attacks typically involve a perpetrator instantly borrowing, swapping, depositing, and then borrowing again to tweak a specific token’s price.
The Steps:
- Attacker takes a flash loan from dYdX for 21k ETH.
- He/she swaps ETH for CHEESE at Uniswap.
- Attacker transfers both tokens into Uniswap for LP tokens.
- The hacker mints sUSD tokens with the LP tokens from Step #3.
- By swapping ETH for CHEESE, the hacker raises the price of CHEESE.
Step #5 was crucial to the hack’s success because it increased the LP token’s collateral value in Cheese Bank. By manipulating the CHEESE-ETH pool, the hacker could drain the DAI, USDC, and USDT with legit borrow( ) calls.
So, with a series of borrow calls at Cheese Bank and swaps at Uniswap, the hacker finished off the job by repaying the flash loan to dYdX and pocketing the rest.
Akropolis Hack, November 12, 2020
A bug in the protocol did not enforce reentrancy protection in Acropolis’s SavingsModule smart contract. Unfortunately, this bug resulted in a loss of 2 million DAI from Akropolis’s YCurve and sUSD pools.

Any Akropolis user can deposit tokens to the Delphi Savings Pools to mint corresponding pool tokens. The core logic for these deposits is in the SavingsModule. But the hacker figured a way to mint pool tokens without any real assets to back them. When he/she redeemed these minted tokens, poof! 2 million DAI vanished.
Once again, this hack kicked off with a dYdX flash loan, quickly followed by a flurry of 17 exploitation transactions. Akropolis has retained a forensics investigative agency to track the money flow. For a more detailed version of this exploit, please see our article on Akropolis.
Value DeFi Hack, November 14, 2020
An attacker hit Value DeFi’s MultiStables vault last month for approximately $7 million with a complex flash loan attack.
Unfortunately, the vault was using some new code that auditors hadn’t inspected. And once again, this attack started with a flash loan (only this time, it was from Aave). The attacker swapped the loan on both Aave and Uniswap for DAI and USDT. He also made subsequent swaps on Curve’s 3pool, which unbalanced it.
With the price feed manipulated, the attacker removed 33 million 3CRV. A couple more slick swaps at Curve and the attacker finished off his day’s labor by burning the 33 million 3CRV for 33 million DAI.
The entire intrusion amounted to a $7 million loss after he paid back Aave’s flash loan. With $2 million in DAI returned to Value DeFi, the profits still exceeded $5 million. But it wasn’t quite over yet. The hacker finished his exploit with a missive to the Value DeFi team, “do you really know flash loans?”
The team has promised to engage in heavy auditing for future vaults while working out a compensation fund for the victims.
Origin Dollar Hack – November 17, 2020
A smart contract bug that did not validate assets transferred in nor enforce reentrancy protection on the mint logic was the culprit here. Because of it, the hacker could inflate the supply of OUSD tokens and help himself to about $8 million worth from the OUSD vault.

The smart contract had already been deemed safe from reentrancy bugs unless the attack came by way of one of the supported stablecoins—which the hacker had figured out. So, he/she could pass off a fake stablecoin as legit, which allowed the reentrancy attack.
The Steps:
- Borrow 70K ETH from dYdX in a Flash Loan.
- Swap 70K ETH for USDT and DAI on Uniswap.
- Move 7.5 million USDT to the Origin vault to mint 7.5 million OUSD.
- Invoke Origin’s mintMultiple method with DAI.
- Smart contracts did not recognize the malicious contract and transferred 20.5 million DAI to their vault.
- A hidden call triggered a rebase of the OUSD supply doubling the attacker’s balance.
- Swap OUSD for USDT on both Uniswap and SushiSwap.
- Withdraw DAI and USDT from the OUSD vault.
- Exchange USDT for ETH on Uniswap.
The attacker repaid the flash loan of 70k ETH to dYdX. He redeemed the OUSD for a mix of stablecoins and converted the USDT and USDC tokens to ETH on Uniswap. This mix, along with the DAI, went straight into his wallet.
The attacker’s prize for this DeFi hack was about $3 million worth of ETH and $2 million in DAI. The funds next went through a money-laundering wash via Tornado Cash, renBTC, and wBTC.
Origin USD is monitoring the addresses for movement and asking exchanges to blacklist any transactions from these wallets while figuring out a compensation plan for the victims.
This hacker now has a $1 million bounty on his head.
Pickle Finance Hack, November 21
PickleJars house yield farming robots earn yield for their users. They are a forked version of Yearn Finance’s v1 vaults, and the attacker succeeded with this exploit because of his knowledge of Yearn’s code.
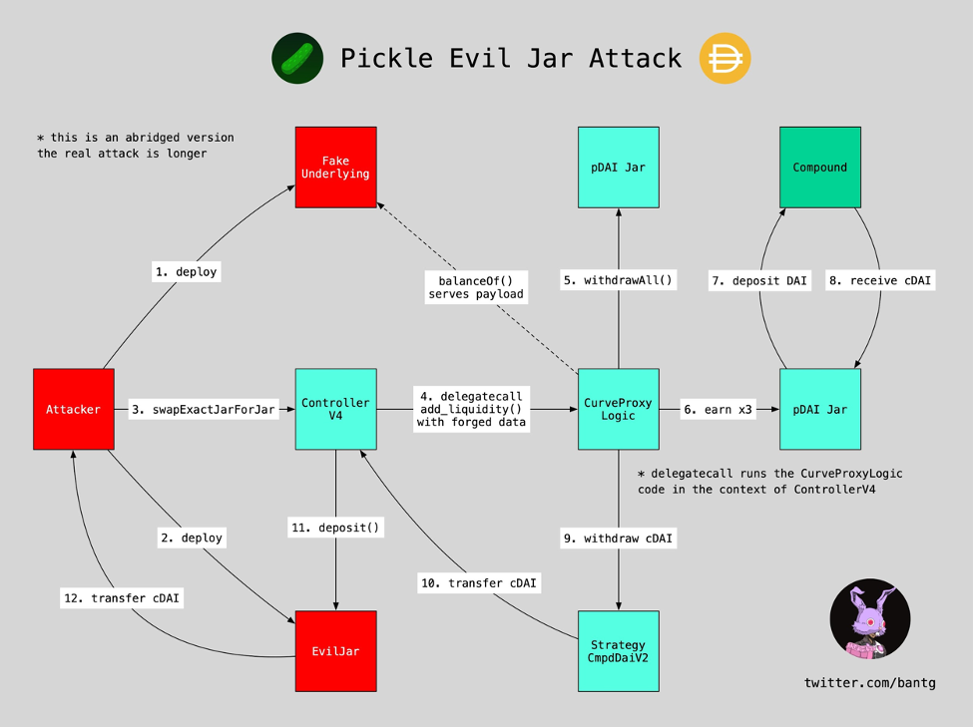
The attack netted close to 20 million DAI by using an “Evil Jar.” But this was a different kind of a hack because the hacker exploited a logic error in the smart contract.
We’ve already covered this exploit in-depth in our Pickle Finance article. Suffice it to say, investigators are monitoring the hacker’s wallet for any movement of the stolen DAI, and fortunately, Pickle has moved on to team up with Yearn Finance.
Warp Finance Hack, December 17, 2020
The year’s hacks seemed to be coming to an end when yet another one succeeded in removing $8 million worth of DAI and USDC from the WarpVaultSC. A bug in the AMM-based price oracle (Uniswap) was once again the culprit, with four different flash loans from dYdX and Uniswap preceding the attack.
The Steps:
- Four different flash loans of DAI and WETH from dYdX and Uniswap.
- Deposits to the WETH-DAI pair on Uniswap to mint LP tokens.
- Transfers the LP tokens to WarpVaultLP as collateral.
- Swaps 341k WETH for 48 million DAI via Uniswap.
This move more than doubled the LP token price allowing the attacker to borrow 4 million DAI and 4 million USDC from Warp. The attacker then returned the flash loans.
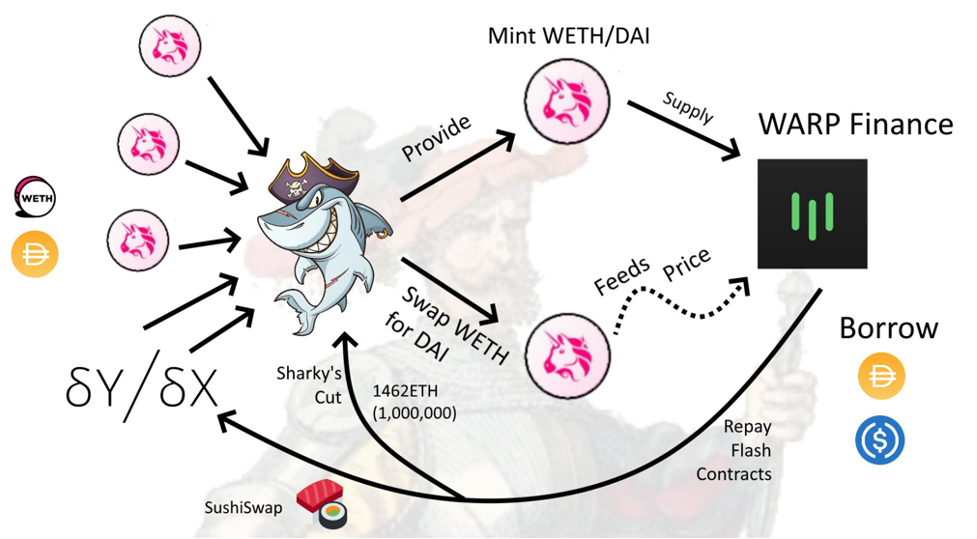
However, even though there is still approximately $8 million at play here, the attacker doesn’t have immediate access to it because WarpFinance has the LP tokens locked due to an under-collateralized loan position.
It looks like this hacking story will have to be continued.
Conclusion
There are other honorable mentions for 2020 DeFi hacks, like Balancer, Eminence, and SushiSwap, but those covered in this article were prominent. After all, SushiSwap only got pinched for a pithy $15k, and they so admired the hacker’s work that they wrote it off as a bug bounty service.
Nonetheless, even with the DeFi ecosystem hardening, its composability will lend itself to ever-increasing risks. DeFi protocols are so interconnected like Lego blocks that a platform is only as secure as its weakest link. One vulnerability in a dApp opens up complications for all the other protocols that are dependent upon it.
To keep new users interested and the regulators at bay, security audits need to become a continuous process. And more importantly, developer resources need to be rigorously updated to keep up with this ever-evolving ecosystem. Nothing is free in this world. So, wherever there is potential for excellent yield, there will always be savvy hackers lurking nearby to make you work for it.
Do you want to learn more about smart contracts and become a top-notch blockchain developer? If so, visit Ivan on Tech Academy today!
Author: MindFrac